Gate.io’s security system is committed to the field of centralized transactions, providing users with multi-dimensional security through decentralized solutions such as Gate Chain and Block Info.
In the world of cryptocurrencies, security is a core issue. At the end of February 2025, incidents of capital theft in the industry occurred frequently, and user asset security once again became the focus of attention.
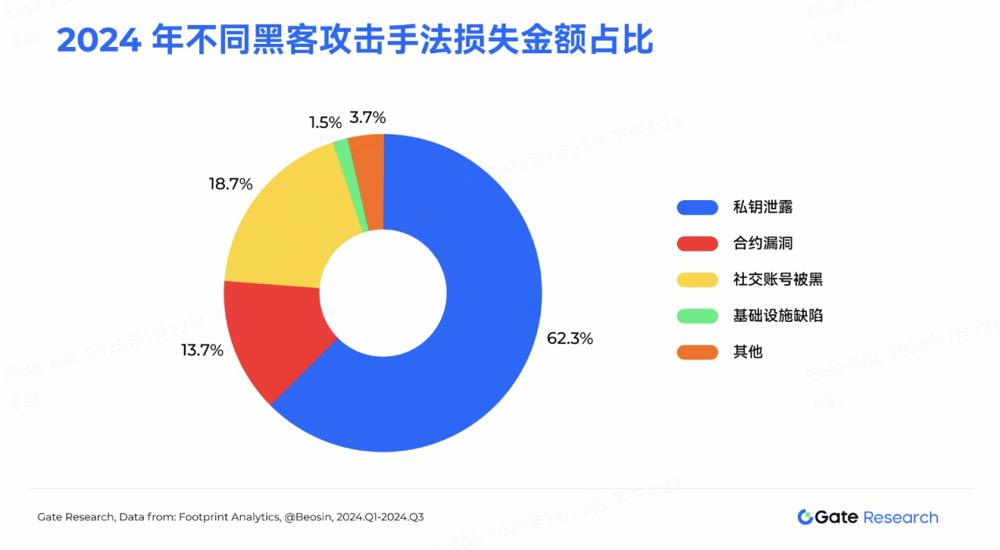
According to the Gate Research Institute, as of November 2024, there have been a total of 1,740 public security incidents in the blockchain ecosystem, with a total loss of US$33.744 billion. Among them, 369 incidents occurred in 2024 alone, causing losses of US$2.308 billion, indicating that hacking has become a persistent threat. In particular, private key disclosure incidents accounted for 62.3% of all losses.
Facing industry challenges, Gate.io always adheres to “safety firstThe core principle of “, relying on leading technology and strict risk control system, builds an unbreakable safety barrier for users.
Top defense system: blocking risks from the root cause
As we all know, technology is the cornerstone of security.Gate.ioKnowing its importance, we have invested heavily in technology research and development to create an all-round and multi-level security protection system.
The independently developed trading system is the core of Gate.io’s security system。Each module iterates independently and undergoes penetration testing by professional companies and annual security audits to ensure that the system remains indestructible in the face of complex attacks. The front end of the system uses protection services provided by many of the world’s leading security companies such as Cloudflare and Akamai to build a solid defense line to keep malicious traffic and attacks out.
In terms of data transmission, Gate.io uses an encrypted Transport Layer Security (TLS) protocol to ensure that all website data is not stolen or tampered with during transmission. This encryption technology is equivalent to putting an “invisible cloak” on user data, making it impossible for hackers to start.
In the face of DDoS attacks, through a four-step mechanism of detection, response, defeat, and recording, the platform builds a self-evolving anti-DDoS attack system to continuously improve its response capabilities.Gate.io’s anti-DDoS mechanism is like a smart shield that can automatically identify and defend against various attacks.
In addition, the platform simultaneously deploys Web Application Firewall (WAF) and DNS security measures to further enhance overall defense capabilities. WAF intelligently identifies and blocks illegal intrusions, data tampering, and vulnerability attacks, while DNS security measures effectively prevent the possibility of hijacking or fraudulent communications.
Strict internal control mechanism: create a safety net that is “watertight”
No matter how powerful the technology is, it also requires strict internal management guarantees.Gate.ioIt is believed that internal security is an important part of the entire platform security system.Therefore, the platform adopts the strictest security management measures to ensure that every link is under monitoring.
All computers are equipped with endpoint protection mechanisms and are fully protected by corporate firewalls. At the same time, the platform is equipped with a zero-trust security architecture to carry out security protection based on the principle of “continuous verification, never trust” to ensure that the software is always kept up to date. It also adopts the principle of minimum authority (PoLP) and role-based access control (RBAC), regularly review and detect redundant account accesses, and strictly implement the access permission application process to ensure that only authorized personnel can access sensitive data, fundamentally reducing security risks.
Development management is also a key part of internal control. Gate.io has established a complete Software Development Life Cycle (SDLC) management system to strictly control the safety and quality of software from the entire life cycle of software requirements design, architecture review, development, continuous integration, continuous deployment, and software operation and maintenance. During the software development process, developers ‘code submissions are strictly audited, and testing technologies such as SAST, SCA, and DAST are also introduced to continuously detect any backdoor code and security vulnerabilities.This strict management process eliminates potential security loopholes from the source and builds an indestructible defense line for platform security.
Account security: Two-factor authentication makes the account airtight
For users, account security is the most concerned issue, and Gate.io has made great efforts in this regard.The login process is the first line of defense for account security. Gate.io provides multiple verification methods such as SMS, Google OTP, IP address monitoring, and email to ensure the authenticity of user identities. The dual protection mechanism of login passwords and fund passwords doubles account security and further strengthens protection.
In the transaction and withdrawal process, each withdrawal requires multiple security certifications, including SMS or email verification. After security settings such as password reset are changed, users cannot withdraw cash within 24 hours. This measure can effectively prevent the possibility of hackers withdrawing funds by tampering with security settings.
Also,Gate.ioIt also provides users with a security log function, so that users can view the login and operation records of their accounts at any time, and once abnormalities are discovered, they can immediately take countermeasures.
Asset protection: Cold and hot wallets are two-pronged, and funds are solid
In the world of digital assets, the security of wallets is directly related to the security of users ‘assets.Gate.io adopts a method of separating hot and cold wallets to provide “double protection” for user assets.
Hot wallets ensure the security of private keys through multiple advanced technologies such as multi-signature, TEE (Trusted Computing), MPC (Multi-Party Computing), threshold signature, and big data risk control. All users ‘recharge and withdrawal needs must pass multiple risk management certifications before being broadcast to the blockchain for confirmation to prevent financial risks.
Cold wallets follow the principles of off-site backup, bank custody, multiple storage media, multiple signatures and complete offline to ensure the absolute security of assets. Over many years of long-term practice, Gate.io has formed a complete management process and emergency response mechanism. The “hot and cold separation” wallet management method maximizes the security of user assets.
Asset reserves: 100% reserve scale is the world’s leading
Through Merkel Tree and zero-knowledge proof (zk-SNARK) technology, Gate.io achieves transparent verification of 100% reserves.
As of January 17, 2025, the total value of Gate.io reserves has reached10.328 billionDollar, reserve ratio as high as128.58%, significantly exceeding industry standards. The platform’s reserves cover more than 200 types of user assets, and the scale of excess reserves is as high as2.296 billionUS dollar, excess reserve ratio reaches28.58%, increase from December last year450mUS dollar, increase by24.38%。
At the same time, Gate.io regularly releases reserve data and conducts audits through the authoritative blockchain security company Hacken to ensure the transparency and security of reserves.
Smart contracts: the “golden eye” of security audits
The security of smart contracts is one of the pain points of the blockchain industry. Gate.io takes “zero tolerance“With the attitude of”, the platform provides automated contract audits to monitor on-chain events in real time to ensure that contract risks are controllable.
At the same time, Gate.io strictly screens high-quality projects, conducts regular safety audits, and signs a declaration of no evil with the project party to monitor the project party’s performance in real time. Through comprehensive security measures, Gate.io provides a solid guarantee for the security of smart contracts and effectively prevents potential risks.
Vulnerability reward plan, global white hat escort
In the security field, loopholes are often the biggest hidden danger. To this end, Gate.io has set up a vulnerability reward program to encourage security researchers to report possible security vulnerabilities on the platform. Through this mechanism, Gate.io can discover and repair potential security issues in a timely manner, further improving the security of the platform.
The vulnerability reward program is an important supplement to Gate.io’s own security system.It not only enhances the protection capabilities of the platform, but also attracts the attention and participation of a large number of security researchers, allowing Gate.io to establish a good reputation in the security field of the encryption industry and win widespread trust and support.
Industry benchmark: Create a comprehensive security solution
Gate.io’s security system is committed to the field of centralized transactions, providing users with multi-dimensional security through decentralized solutions such as Gate Chain and Block Info.
This comprehensive security solution has allowed Gate.io to reach new heights in the field of security.Gate.io not only protects the security of users ‘assets, but also sets a security benchmark for the entire industry.”
Take security as your belief and build the cornerstone of trust
Gate.io builds an unbreakable “iron wall” for users through a series of hard-core security measures. From technical escort to internal control, from account protection to asset protection, from compliance transparency to smart contracts, to vulnerability rewards and comprehensive security solutions, Gate.io has always pursued the ultimate in the field of security.
Looking to the future, Gate.io will continue to strengthen technological innovation, improve the security system, and provide users with a more secure, reliable and transparent transaction environment.Gate.io’s goal is to allow every user to trade with peace of mind, and to make “security” synonymous with Gate.io.
disclaimer: This content does not constitute any offer, solicitation, or recommendation. You should always seek independent professional advice before making any investment decisions. Please note thatGate.ioAll or some services from restricted areas may be restricted or prohibited. Please read the user agreement for more information, link:https://www.gate.io/zh/user-agreement。



