On February 27, Bybit released a hacker forensics report. The investigation pointed out that the theft of funds was caused by Safe infrastructure vulnerabilities, but it seemed that Safe was unwilling to accept the accusation.
Author: Frank, PANews
On February 21, 2025, the cryptocurrency exchange Bybit suffered an epic hacking attack, and assets worth US$1.46 billion were stolen by the North Korean hacking organization Lazarus. In addition to recovering assets, it is more important to identify the attack path to avoid new attacks. On February 27, Bybit released a hacker forensics report, and the investigation pointed out that the theft of funds was caused by Safe infrastructure vulnerabilities. But it seems Safe is unwilling to accept the accusation. In the statement, he admitted that the developer was hacked, but blamed the main reasons on the clever methods of North Korean hackers and Bybit’s operational errors. The “Rashomon” staged in the discussion of who has greater responsibility has also triggered a big debate in the industry over infrastructure trust, security paradigm and the game of human nature.
The attack originated from the attack on Safe{Wallet} front-end cloud service
According to two investigation reports released by Bybit (Bybit Incident Preliminary Report and Bybit Interim Investigation Report), further analysis of Safe{Wallet} resources found two snapshots of JavaScript resources taken on February 19, 2025. A review of these snapshots revealed that the first snapshot contained raw, legal Safe{Wallet} code, while the second snapshot contained resources with malicious JavaScript code. This suggests that the malicious code that created the malicious transaction originated directly from Safe{Wallet}’s AWS infrastructure.
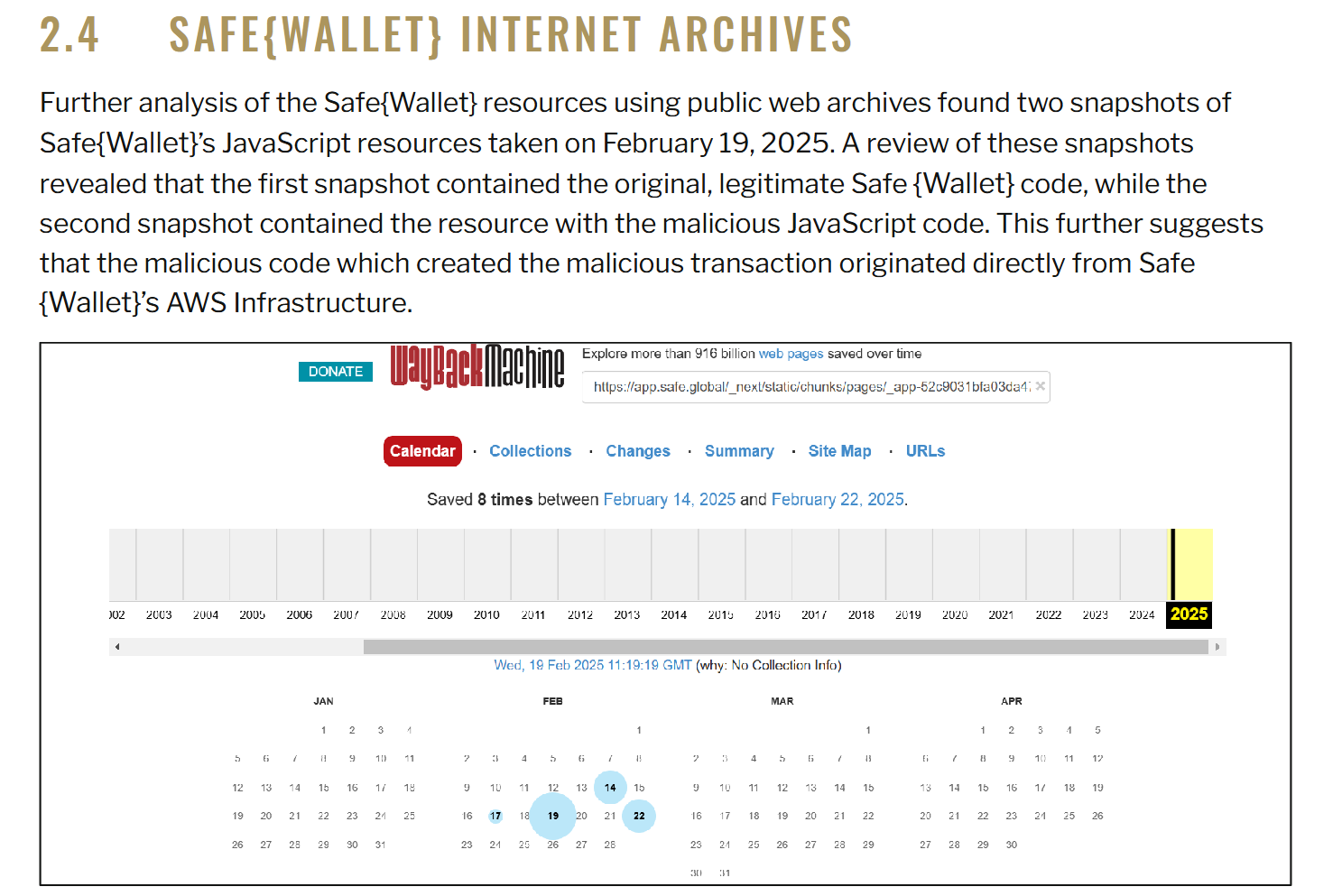
The report’s conclusions show: Based on the results of an investigation into Bybit’s signer machines and the discovery of cached malicious JavaScript payloads in the Wayback Archive, we strongly conclude that Safe.Global’s AWS S3 or CloudFront account/API keys may have been compromised.
To sum up, the initial source of this attack was that hackers attacked Safe{Wallet} developers ‘devices, tampered with front-end JavaScript files in the AWS S3 bucket, and implanted targeted malicious code targeting the Bybit cold wallet address. Previously, Safe also issued a simple investigation report stating that no code vulnerabilities and malicious dependencies (i.e. supply chain attacks) were found. Safe then conducted a comprehensive review and suspended the Safe{Wallet} feature. The results of this investigation seem to overturn Safe’s previous findings.
Safe’s statement raises more questions
Bybit has not expressed its position on Safe’s responsibility for this incident so far, but after the report was released, social media began to discuss Safe’s security vulnerabilities, and some voices believed that Safe should be responsible for this and pay compensation.
Safe officials obviously do not approve of this report. In its official statement, Safe divided its responsibilities into three levels: technical aspects, emphasizing that smart contracts were not attacked, and emphasizing product security. In terms of operation and maintenance, it admitted that the developer’s equipment was hacked and the AWS key was leaked, but blamed it on a national-level attack by a North Korean hacker organization. On the user side, users are advised to be vigilant when signing transactions, implying that Bybit has not fully verified the transaction data.
However, this response is suspected of avoiding important issues and addressing minor issues. According to the process shown in the report, Safe made the following mistakes in this process:
1. Out of control of privileges: The attacker obtained AWS privileges by invading the developer’s device, exposing the Safe team to not implement the minimum privilege principle. For example, a developer can directly modify production environment code without a code change monitoring mechanism.
2. Front-end security dereliction: Basic protective measures such as SRI (Sub-Resource Integrity Verification) are not enabled.
3. Supply chain dependence risk: The attack path (developer equipment →AWS→ front-end code) proves that Safe relies too much on centralized cloud services, which conflicts with the decentralized security concept of blockchain.
In addition, the industry has also raised many questions about Safe’s statement. Binance founder CZ has raised five technical questions in a row (such as the specific way in which the developer’s equipment was hacked, the reasons for the loss of authority, etc.), pointing directly to the opacity of Safe’s statement. Safe did not disclose the details of the attack chain, making it impossible for the industry to defend itself in a targeted manner.
Coins rise strangely, daily activity drops by nearly 70%
Another big controversy in the community is whether Safe should compensate Bybit for the losses in this incident. Some users believe that Safe’s infrastructure vulnerability caused the attack, and Safe should be responsible for compensation. What’s more, it is proposed that Safe’s predecessor company, Gnosis, bear joint and several liability for losses. Safe was originally a multi-signed agreement developed by Gnosis Safe by the Gnosis team in 2017 and will be spun off and operated independently from the Gnosis ecosystem in 2022. Gnosis completed ICO financing of 250,000 ETH in 2017, and currently has 150,000 ETH in its treasury, belonging to the ETH giant whale.
However, some people believe that the main responsibility for this incident still lies with Bybit itself. On the one hand, it is necessary to invest in research and development efforts to develop a series of security infrastructure. On the other hand, Bybit seems to be using the free Safe service and does not pay a subscription fee, so Safe is not obligated to bear responsibility from this perspective.
After publishing the investigation report, Bybit did not request Safe to provide financial compensation.
While the industry is still debating responsibility, the capital market is playing an absurd drama. Safe’s official token seems to have attracted special attention due to this incident. On February 27, SAFE token bucked the trend from US$0.44 to US$0.69, with a maximum increase of about 58% in 10 hours. However, from the perspective of investment logic, the incident has mainly had a negative impact on Safe’s brand, and the increase may be just due to short-term market sentiment.
Data on February 27 showed that Safe’s total assets under management exceeded US$100 billion, and its silence on the details of the vulnerability is shaking its credibility as an industry infrastructure.
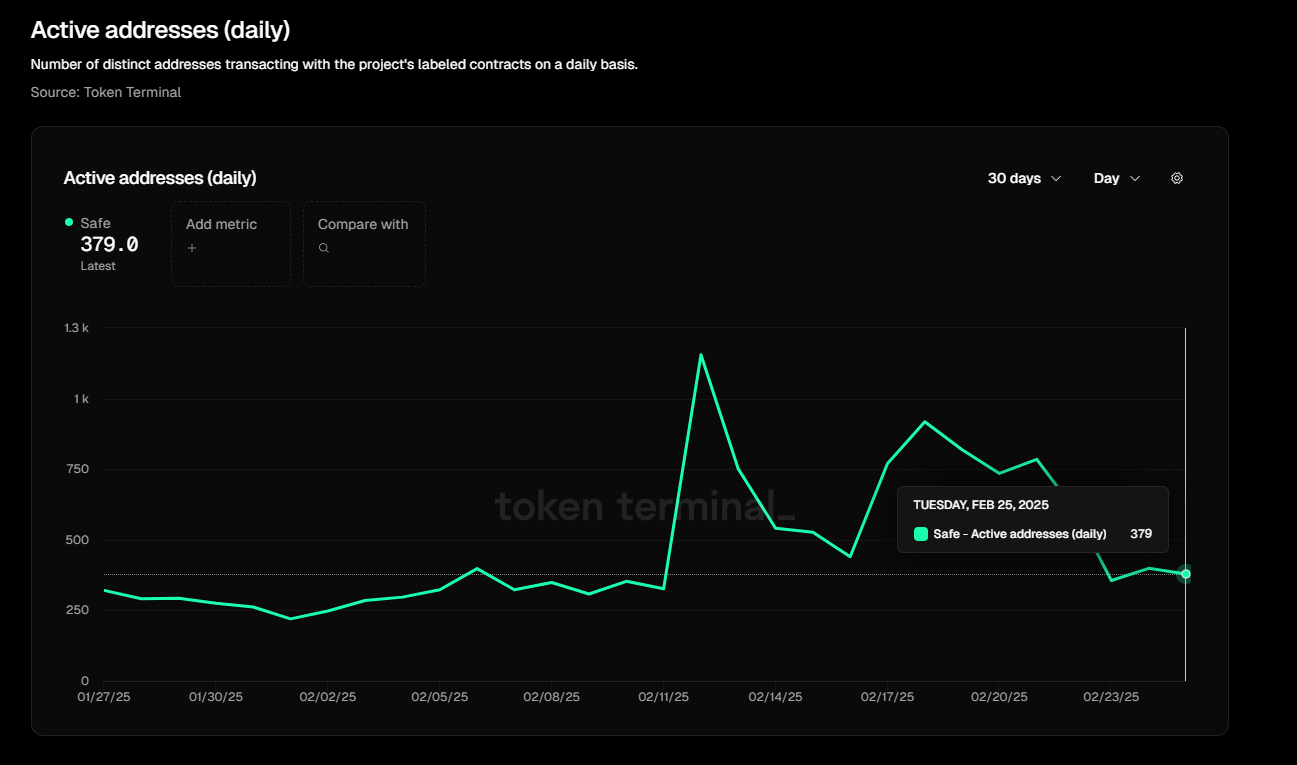
In terms of daily active user data, it can be clearly seen that Safe has suffered a considerable impact after this incident. Compared with the 1200 daily active addresses on February 12, the data dropped to 379 daily active addresses on February 27, a drop of nearly 70%.
 In addition, after the centralized risks of the front-end were exposed, the community once again paid attention to the front-end security mechanism. ICP founder Dominic Williams said that the North Korean hacker group recently successfully stole US$1.5 billion in Bybit funds, mainly using Safe{Wallet}’s Web-side vulnerability, which is hosted in the cloud rather than on a smart contract. Williams criticized that some Web3 projects only run on the “fake onchain”, causing security risks, and suggested using ICP (Internet Computer) for on-chain computing, data storage, and user experience verification to improve security. He proposed migrating Safe{Wallet} to ICP and adopting cryptographic authentication mechanisms and multi-party consensus governance (such as SNS DAO) to enhance security.
In addition, after the centralized risks of the front-end were exposed, the community once again paid attention to the front-end security mechanism. ICP founder Dominic Williams said that the North Korean hacker group recently successfully stole US$1.5 billion in Bybit funds, mainly using Safe{Wallet}’s Web-side vulnerability, which is hosted in the cloud rather than on a smart contract. Williams criticized that some Web3 projects only run on the “fake onchain”, causing security risks, and suggested using ICP (Internet Computer) for on-chain computing, data storage, and user experience verification to improve security. He proposed migrating Safe{Wallet} to ICP and adopting cryptographic authentication mechanisms and multi-party consensus governance (such as SNS DAO) to enhance security.
Looking back at the entire incident, it seems to be an isolated incident carefully planned by North Korean hackers, but it still exposes security loopholes in Safe’s current multi-signature wallet in terms of authority design and supply chain. From the perspective of brand development, the rush to clear up the blame in order to deliberately maintain safety myths is also counterproductive, but has triggered more doubts from public opinion. Perhaps Safe’s ability to admit mistakes in a timely manner and launch corresponding measures can better reflect the attitude of giants in the field of encryption security. At the same time, announcing the details of vulnerabilities as soon as possible can further help the industry strengthen self-examination and prevention of similar vulnerabilities.



