Based on the analysis and demonstration of 100 projects.
Author: 0x Lao Dong
Core rules for project parties to screen users
When designing airdrop strategies, project parties rarely screen based on a single criterion. Instead, they evaluate the quality of users from multiple dimensions to ensure that airdrops can be delivered to truly valuable addresses. From the perspective of the project side, their favorite is High TVL, high net worth users, as well as long-term participation in ecological construction Real active users。Based on these principles, combined with the strategies of historical airdrop projects, Lao Dong summarized several core screening dimensions.
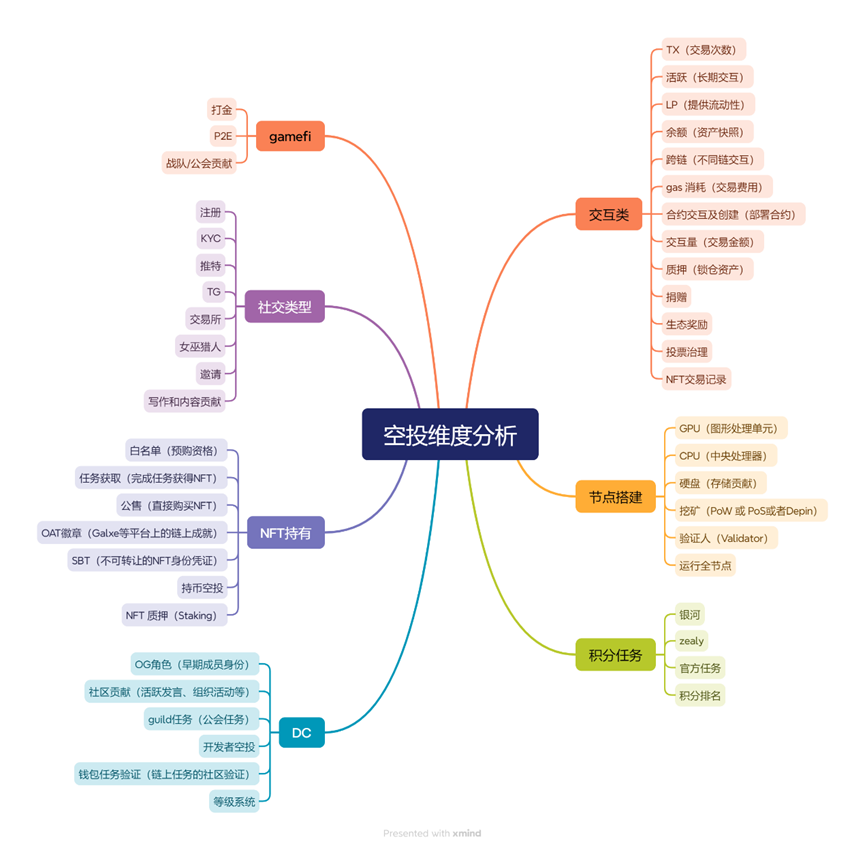
1️⃣Interactive Screening Criteria
-
Number of transactions, transaction volume and activity: Reflecting the level of activity of users on the chain, frequent transactions and in-depth interactions indicate that users have a certain investment in the ecosystem, but excessive data may also be a brushing behavior. For example, Starknet W makes more mistakes;
-
Gas consumption: The total transaction fees paid by users can reflect their actual participation and actual contribution. For example, Zkfair distributes the current morph of the airdrop through gas consumption, and distributes points through gas;
-
Contract interactive creation: It can be used to measure whether users participate in multiple ecological projects, helping to distinguish real users from those who simply swipe. For example, arb zksync has a weighting of the number of contract interactions;
2️⃣NFT &Asset Category Screening Criteria
-
Whitelist, public sales, task acquisition: Generally, such NFTs are limited and can control deflation. As a token of airdrops, they also represent a high degree of user participation in the project. For example, XAI issues airdrops based on NFT;
-
OAT badges andSBT: As an on-chain achievement or a non-transferable identity certificate, it can effectively prove the user’s long-term contribution and true participation. For example, Odos ‘pilot OAT and LXP from Linea;
-
Holding currency airdrops,NFTpledge: Holding tokens or pledging NFT not only shows users ‘trust in project assets, but also may bring additional incentives, and also helps evaluate users’ asset quality and risk control. For example, NFT airdrop tokens from MOCA and PENGU;
3️⃣Points Task and Task Platform
-
Points accumulation and ranking: Earn points for completing tasks through platforms such as Galxe, Zealy or the official itself. The higher the points, the higher the participation; at the same time, the point ranking can be used as an important basis for airdrop allocation. For example, IO’s Galaxy Points Mission, SCA’s Points Airdrop, and many LSD projects’s Points Airdrop;
-
Cross-ecological tasks: Require users to complete tasks on multiple platforms or ecosystems to more comprehensively assess users ‘overall activity and ecological contribution. For example, many odyssey tasks, move, and linea need to complete many ecological tasks to obtain rewards;
4️⃣Community and social contribution
-
Twitter/Discord/Telegramactive: Users complete social tasks in the community, tweet and forward, etc., or DC, TG speak, participate in discussions, and do some translations for social purposes, so as to obtain corresponding identities. This type of task is more complex and has high airdrop value. For example, the current kaito earns points through tweets and interactions, and move’s gorilla character is worth several thousand U. Dogs issue airdrops based on TG’s account age and activity;
-
Early members (OGRole) and invited contributions: Users who join early or gain new offers through invitations are more likely to receive airdrops to encourage long-term participation, such as the OG character of IP with thousands of tokens airdrops;
-
Content creation and social media interaction: Promotion and discussion on Twitter, Medium, YouTube and other platforms help spread the project and also reflect users ‘sense of identity with the project. For example, the creator role of move;
5️⃣Node building and technical contribution
-
Full node, mining, verifier: Technical participation, such as running nodes, participating in mining or serving as verifiers, directly supports network security and performance and is a highly valued contribution by the project party. For example, IO workers use GPU to dig points, nillion nodes run through CPU, and grass uses IP and traffic to obtain points;
6⃣GameFi and entertainment interaction
-
Gold farming, P2E: Earning tokens through in-game tasks in the GameFi project not only reflects user engagement, but also demonstrates user dependence on the project’s entertainment ecosystem. For example, CATI raises cats to make money in tokens. Large-scale game bigwww.gushiio.com In-game gold mining to earn tokens.
ˇAttack and defense confrontation: witch detection, anatomy and countermeasures
The project party’s witch identification strategy
previous postdata analysisAmong the 100 projects in 2024, 32% will explicitly investigate witches.
In airdrop activities, the project party’s investigation of the core nature of witches is also a screening method to filter outHigh-quality, authentic and highly contributing addressesAvoiding airdrops from being occupied by large-scale and low-quality addresses is not just for studios. Even individual users may be regarded as witch addresses due to reasons such as inability to interact continuously. Just as project parties continue to optimize screening rules, there are still studios that can get good results.
Therefore, understanding the project party’s methods of investigating witches and adopting corresponding defense strategies is the key to ensuring good results. Here Lao Dong listed someMore obvious types of witch risks:
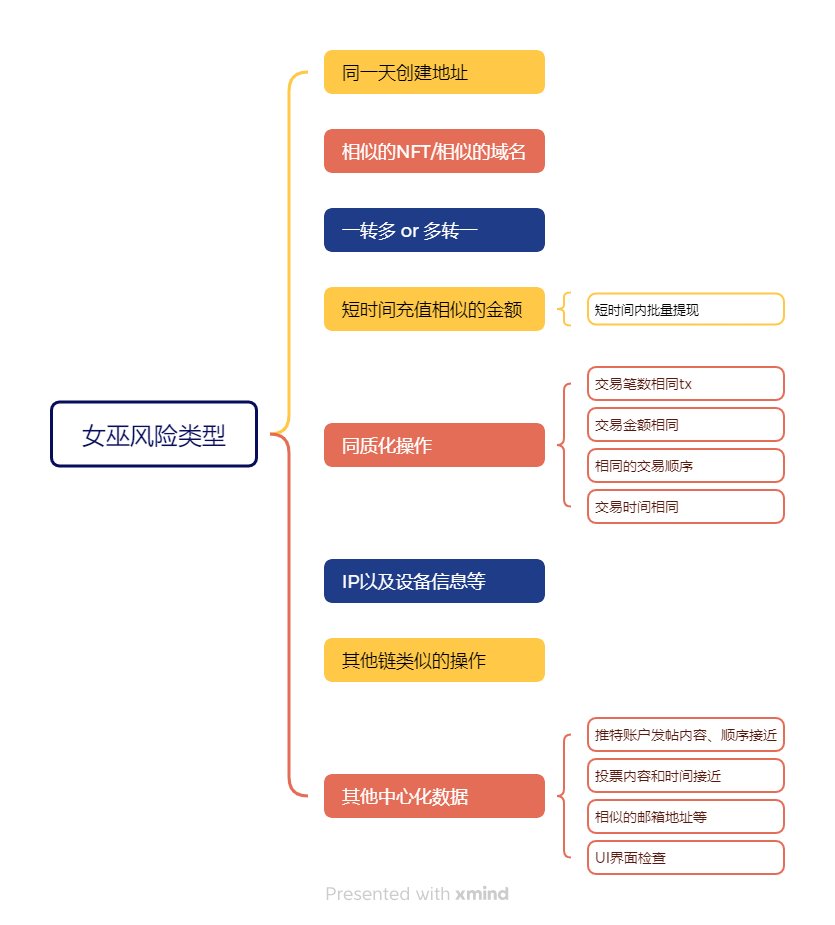
Witch Defense Tactical Manual
1️⃣ Address creation abnormal fund flow
The project party will give priority to checking the address creation time, recharge path, and fund collection. This kind of address aggregation behavior is one of the easiest methods for witches to be investigated. The main methods include:
-
Create multiple addresses on the same day: If a large number of new addresses are created and charged on the same day, they can easily be marked as batch witch accounts.
-
One transfer to multiple or one transfer to multiple accounts: Transfers from the same address to multiple accounts, or funds from multiple addresses are collected into the same wallet, are considered abnormal in fund allocation.
-
Recharge similar amounts in a short period of time: If multiple addresses recharge the same or close amount at similar times, it may be determined that the same controller operated.
-
Bulk withdrawals in a short period of time: If funds from multiple addresses are withdrawn into the same wallet at the same time, it is a high-risk behavior.
💡Prevention strategies:
-
When creating a new address, create a small number of accounts every day and randomly select the recharge time to avoid centralized operations.
-
Use CEX (Binance, OKX, etc.) sub-accounts as transit points to avoid direct collection on the chain.
-
The amount and time of fund recharge should be randomized to avoid batch operations with fixed amounts and fixed times.
-
Open time intervals when withdrawing cash and try to use different CEX sub-addresses to withdraw cash.
2️⃣ Abnormal interaction behavior on the chain
The project party will analyze the interaction pattern of the address, which is collectively referred to as homogeneous interaction, focusing on the following behaviors:
-
Similar NFT or domain name: If multiple addresses receive the same NFT or domain name, it can easily be identified as a batch operation.
-
Similar transaction times: The number of interactions and interactive contracts of multiple addresses are similar, which can easily be determined as robot operations.
-
Same transaction order transaction amount: If the interaction order, amount, and transaction object of the address are the same, it is likely to be identified as a batch account number.
-
Fixed time interaction: If the interaction time of multiple addresses is concentrated in a certain period of time (such as completing a task within 24 hours), the risk is higher.
💡Prevention strategies:
-
Use different accounts to complete different tasks, increase interaction time, and avoid performing the same operations at the same time.
-
Insert smoke bomb projects during interactions, such as participating in some DEX interactions and low-cost dapps such as borrowing, making the behavior on the chain more natural.
-
Randomly interact with different contracts. Don’t all accounts interact with the same DEX, bridge, and contract. Select some addresses and interact with some contracts.
-
Interact at different times 24 hours a day, and interact at random times, rather than batch synchronization operations at fixed times.
3️⃣ IP and under the chaindata analysis
In addition to on-chain data, the project party will also analyze IP addresses, UI interface interactions, browser fingerprints, and social media data, and screen witches through off-chain data:
-
Same IP /same device: If multiple accounts use the same IP or the same browser fingerprint, the risk of being detected as the same person is extremely high;
-
Similar social media behavior: If multiple Twitter accounts have similar posting content, likes order, and interaction patterns, they will easily be excluded by the project party. DC is inactive and kicked out of the channel;
-
Mailbox association: Multiple accounts use similar mailbox naming rules, which may trigger risk control;
-
UI interface inspection: Interaction directly through the contract, but not in the project’s UI interface, some projects will trigger risk control, such as Dianyang;
💡Prevention strategies:
-
Use proxy IP and fingerprint browser to change device information;
-
Pay attention to the randomness of social interactions when raising a number and avoid homogeneous content;
-
Use different email addresses to register and avoid overly similar email names;
-
Try to use front-end interactive scripts to avoid checking the UI interface;
Gradient strategy: Reasonably allocate accounts to reduce the risk of killing
In order to improve the success rate of airdrops, it is recommended to adopt a gradient strategy to divide accounts into different categories to prevent all accounts from being blocked in conjunction with the same model.
At present, project parties are increasingly favoring high-quality numbers. The difference between the lowest and highest addresses of ZK is 100 times, and the difference between STRK and ARB is 20 times.
From ZK’s perspective, if you make 100 high-quality accounts, it is equivalent to the income of 1W low-income accounts. It can reduce energy in operation and also reduce the risk of witches.
But at the same time, subsistence allowance numbers and lottery numbers are also necessary. For example, Tensor, Magic Eden are victories belonging to subsistence allowance numbers, and HMSTR is victories belonging to lottery numbers. The sun shines brightly. Different strategies are chosen, and the final results are completely different.
Premium number (excluding cost, key number)-at least the top 1% in all dimensions
-
High-quality interaction, participating in multiple ecosystems, binding social accounts, and providing proof of humanity such as gitcoin;
-
Individuals use wallets in small quantities but high-quality products to increase the contribution to the ecosystem on the chain;
-
Simulate real user behavior, operate for a long time, and avoid one-time airdrops;
✅ Low-income guarantee (minimum airdrop threshold, moderate operation)-at least the top 20% in all dimensions
-
Only participate in core airdrop missions and do not perform obvious witch operations;
-
Trade in moderation to avoid too frequent or regular interactions;
Lottery number (lot number, low-cost trial and error)
-
Only do simple and cost-effective tasks and strictly control costs;
-
A more aggressive and unrestrained strategy may be adopted, but it will not affect the main account;
🧠Conclusion
In the current environment where AI+ on-chain analysis technology is developing rapidly, the detection methods of witches are becoming more and more accurate, and simple batch operations are no longer effective.
Therefore, for the studio, witch operations need to have higher randomness and real-life simulation. At the same time, strategies need to be flexibly adjusted, combining methods such as gradient accounts, decentralized interactions, and optimizing fund paths to reduce the probability of being blocked.
For individuals, if they do not have the operating capabilities of the studio team, it is recommended to operate a small number of boutique accounts in a refined manner to increase the revenue of airdrops by participating in multiple ecosystems, increasing social activity, and building a real identity chain. Only by knowing each other, mastering the core screening logic, and flexibly adjusting the operating methods can we remain invincible in airdrop activities!
Welcome to join the official social community of Shenchao TechFlow
Telegram subscription group: www.gushiio.com/TechFlowDaily
Official Twitter account: www.gushiio.com/TechFlowPost
Twitter英文账号:https://www.gushiio.com/DeFlow_Intern



